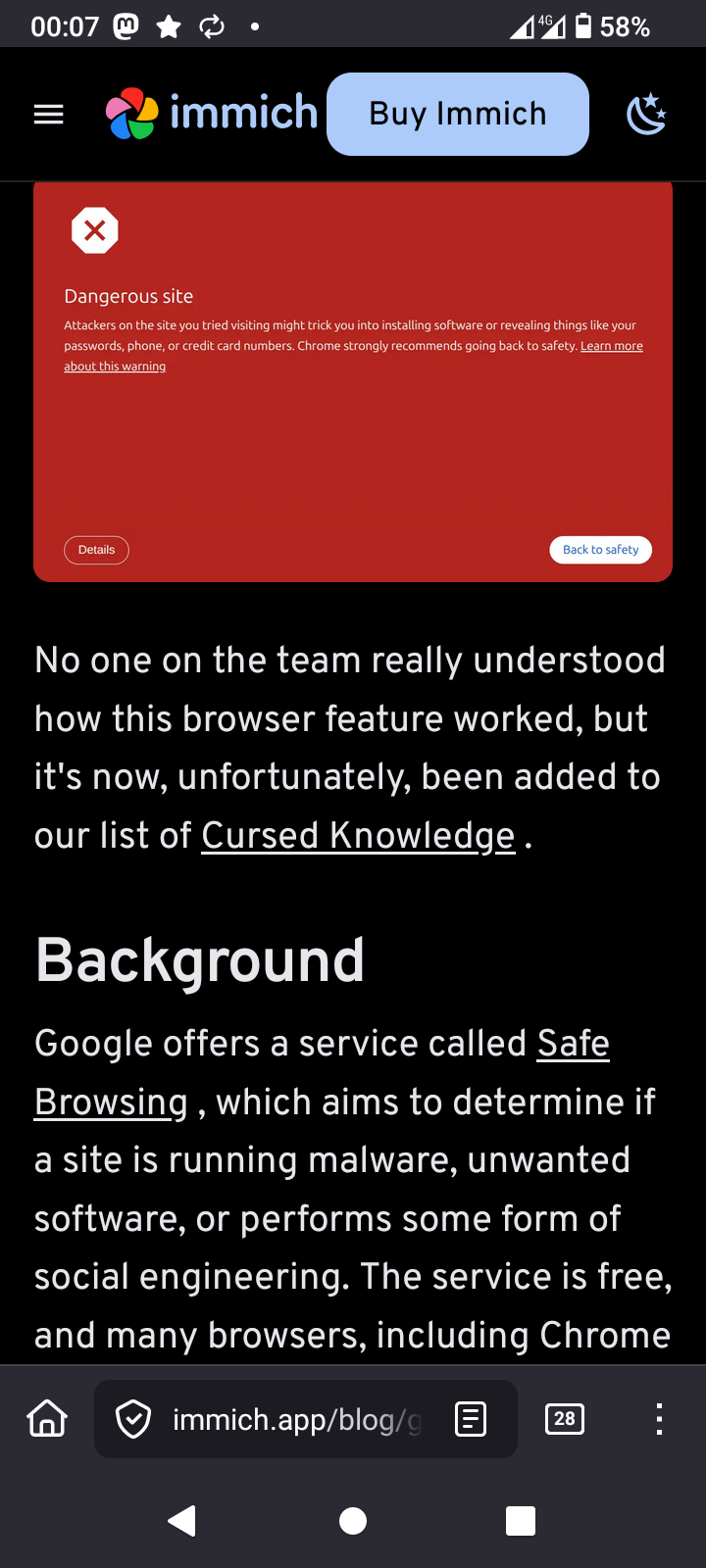
I'm starting to detect the breakdown of what Google has done when it comes down to authentication of programmers for its Android platform
I needed to patch a very small program through fDroid KDE connect
When I proceeded with install, Google Play popped up a bogus requester stating that the program is malicious.
It's not malicious it's an Open Source program
I proceeded with install anyway for which I had to put in my phone's password. Google Play decided to block me from updating the program. I proceeded with this 16 times and got the same result.
I have to check what happens on my other Androids, however on this Android, a small one, I cannot update kdeconnect anymore, because the Play Store actively blocks it even when I override it with install anyway.
KDE connect was installed via fDroid
I have the right to install any program I want, on my device.
I paid for it!
Google cannot dictate me what to do
I shall fight this
@kde @stefano @vermaden
#OpenSource #programming #technology #Google #play #bully #war #fDroid #KDE #network #malicious #bogus