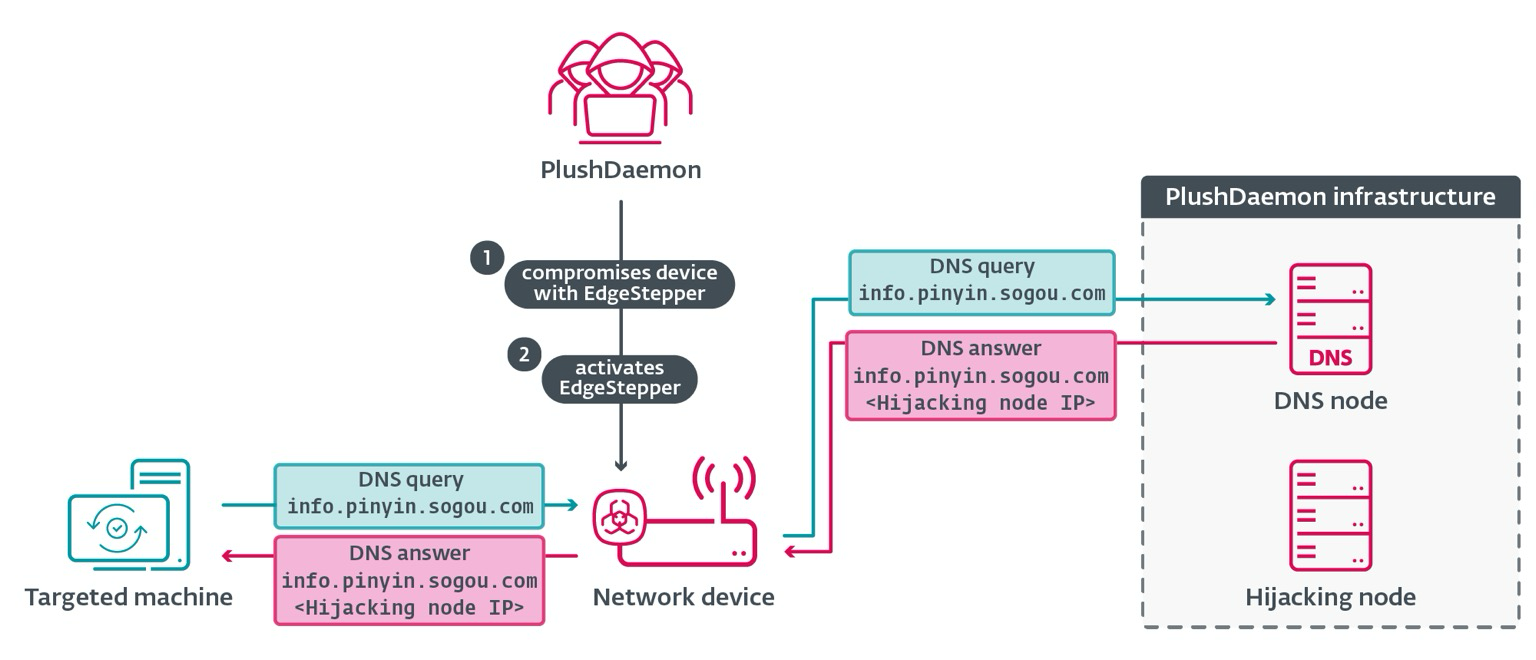
#ESETresearch discovered and analyzed a previously undocumented malicious tool for network devices that we have named #EdgeStepper, enabling China-aligned #PlushDaemon APT to perform adversary-in-the-middle to hijack updates to deliver malware. https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-network-devices-for-adversary-in-the-middle-attacks/
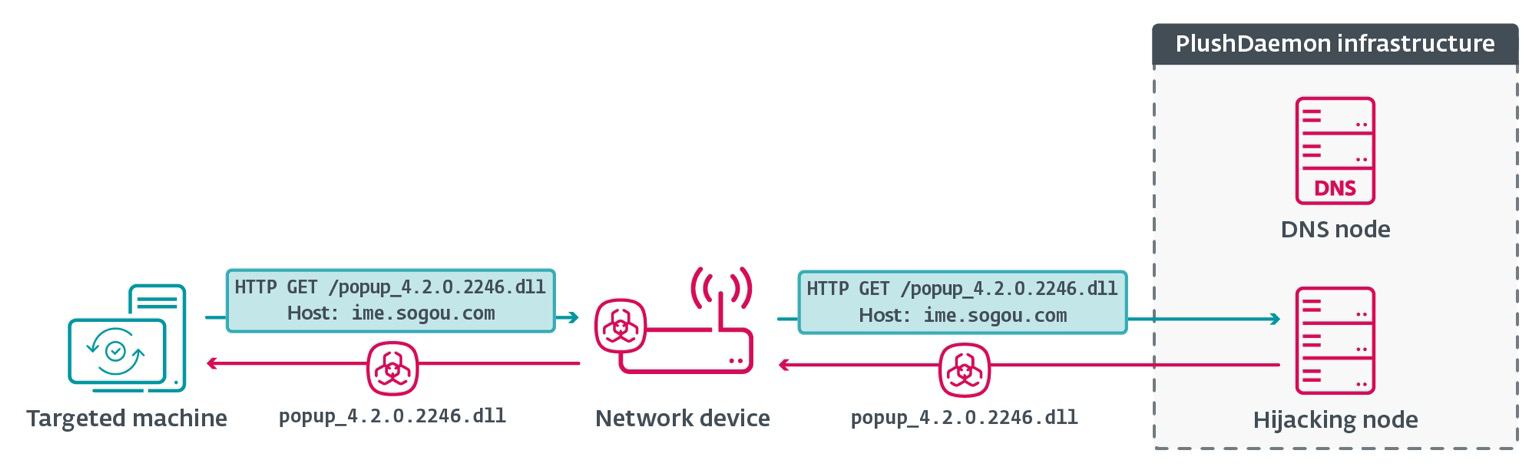
When a network device (e.g., a router) is compromised, EdgeStepper begins to redirect all DNS queries to a malicious DNS node that replies with the IP address of the node that performs update hijacking of popular Chinese software such as Sogou Pinyin Method.
When the software communicates with the hijacking node, it issues instructions to download an update for a DLL; in reality, the downloaders that we call LittleDaemon and DaemonicLogistics ultimately deploy the #SlowStepper backdoor.
#SlowStepper is a feature-rich backdoor with a toolkit of more than 30 components. We analyzed and documented it in a previous blogpost about the compromise of a South Korean VPN service provider. https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-supply-chain-korean-vpn-service/
IoCs available on our GitHub repo: https://github.com/eset/malware-ioc/
2 media