#ESETresearch discovered a new #MuddyWater campaign targeting critical infrastructure in 🇮🇱 Israel and 🇪🇬 Egypt, using a new backdoor – MuddyViper – and a variety of post-compromise tools https://www.welivesecurity.com/en/eset-research/muddywater-snakes-riverbank/
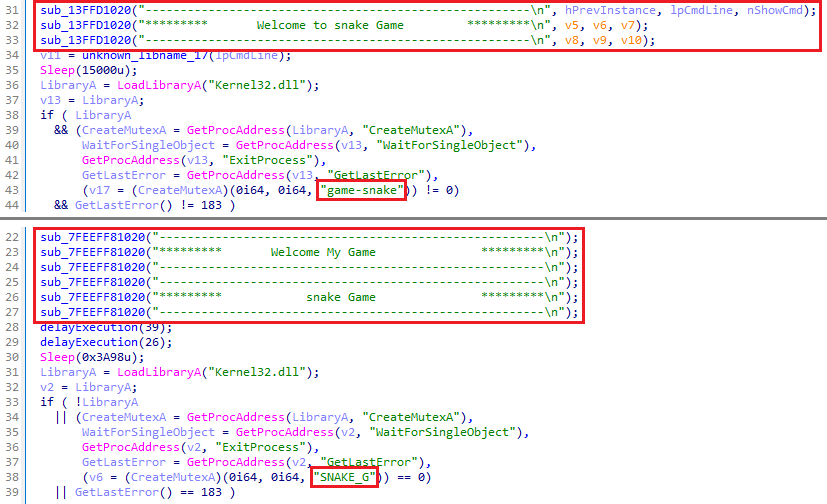
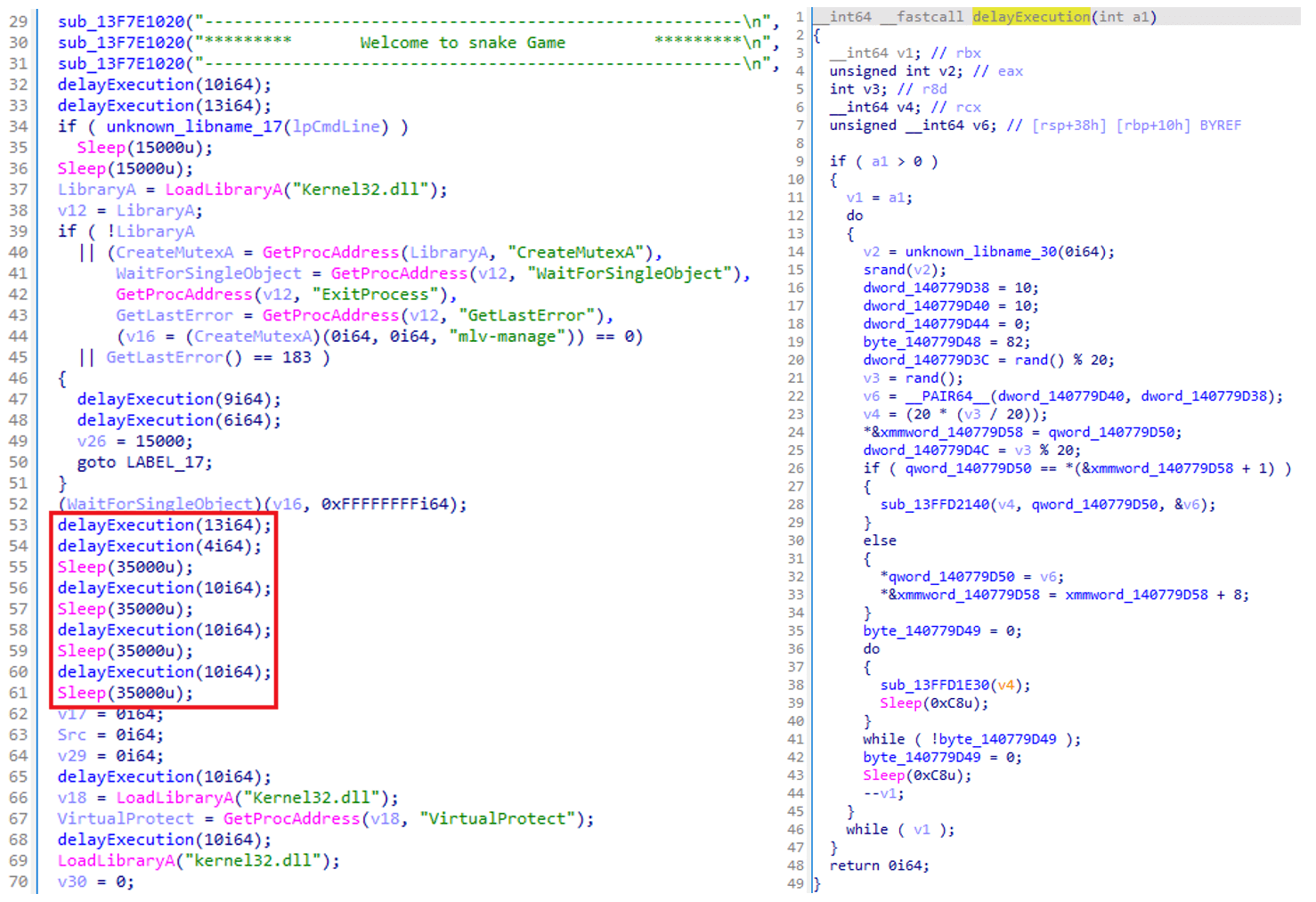
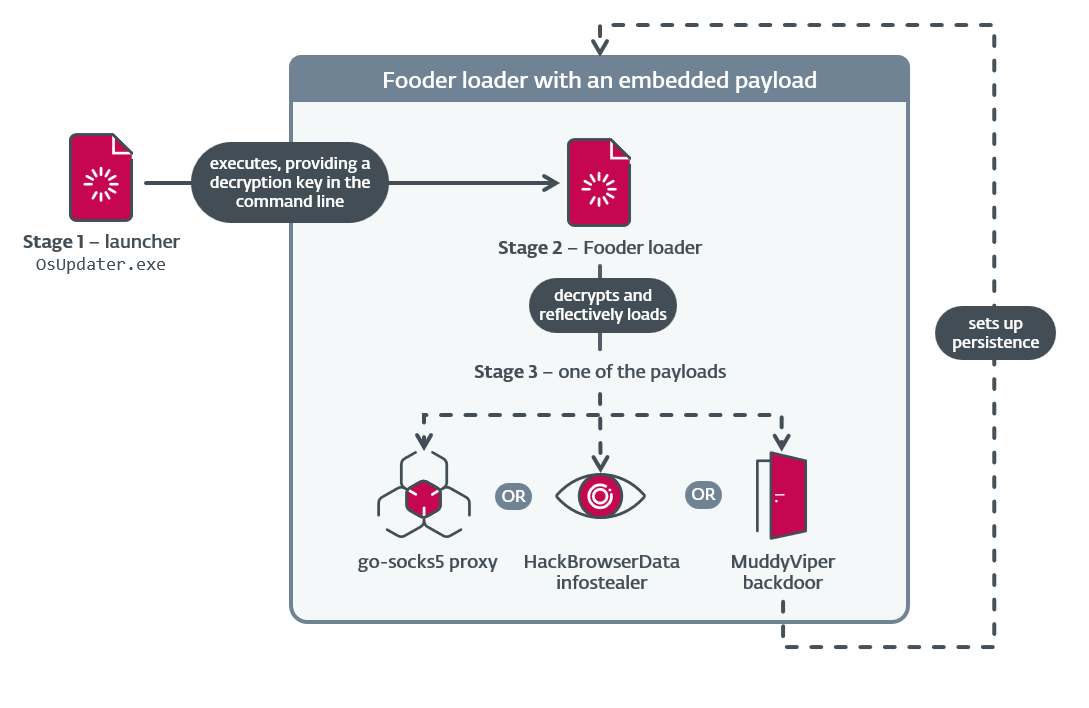
The group used a custom loader, Fooder, which masquerades as the classic Snake game. Its internal logic mimics the game mechanics to delay execution and hinder automated analysis.
Fooder loads MuddyViper, a new C/C++ backdoor that facilitates covert control over compromised systems, the HackBrowserData infostealer, or go-socks5 reverse tunnels that allow attackers to route traffic through compromised machines to obscure the location of its C&C servers.
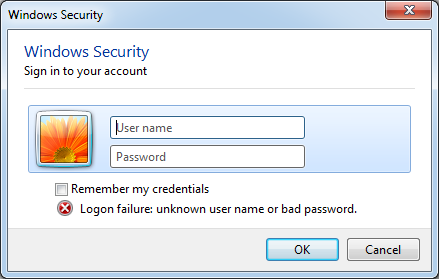
MuddyViper capabilities include operating a reverse PowerShell or Windows Command Prompt, downloading or uploading files in size-limited chunks, stealing data from a variety of browsers, and displaying a fake Windows Security dialog to trick victims into entering credentials.
The post-compromise toolset also includes multiple credential stealers: CE-Notes, which targets Chromium-based browsers; LP-Notes, which stages and verifies stolen credentials; and Blub, which steals login data from Chrome, Edge, Firefox, and Opera browsers.
While some components remain noisy and easily detected, as is typical for MuddyWater, overall this campaign shows signs of technical evolution – increased precision, strategic targeting, and a more advanced toolset.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/muddywater
4 media