#ESETResearch has identified two campaigns targeting Android users in the 🇦🇪. The campaigns, which are still ongoing, distribute previously undocumented spyware impersonating #Signal and #ToTok via deceptive websites. https://www.welivesecurity.com/en/eset-research/new-spyware-campaigns-target-privacy-conscious-android-users-uae/
The first campaign deployed Android #ProSpy camouflaged as upgrades or plugins for Signal and ToTok apps, named Signal Encryption Plugin or ToTok Pro.
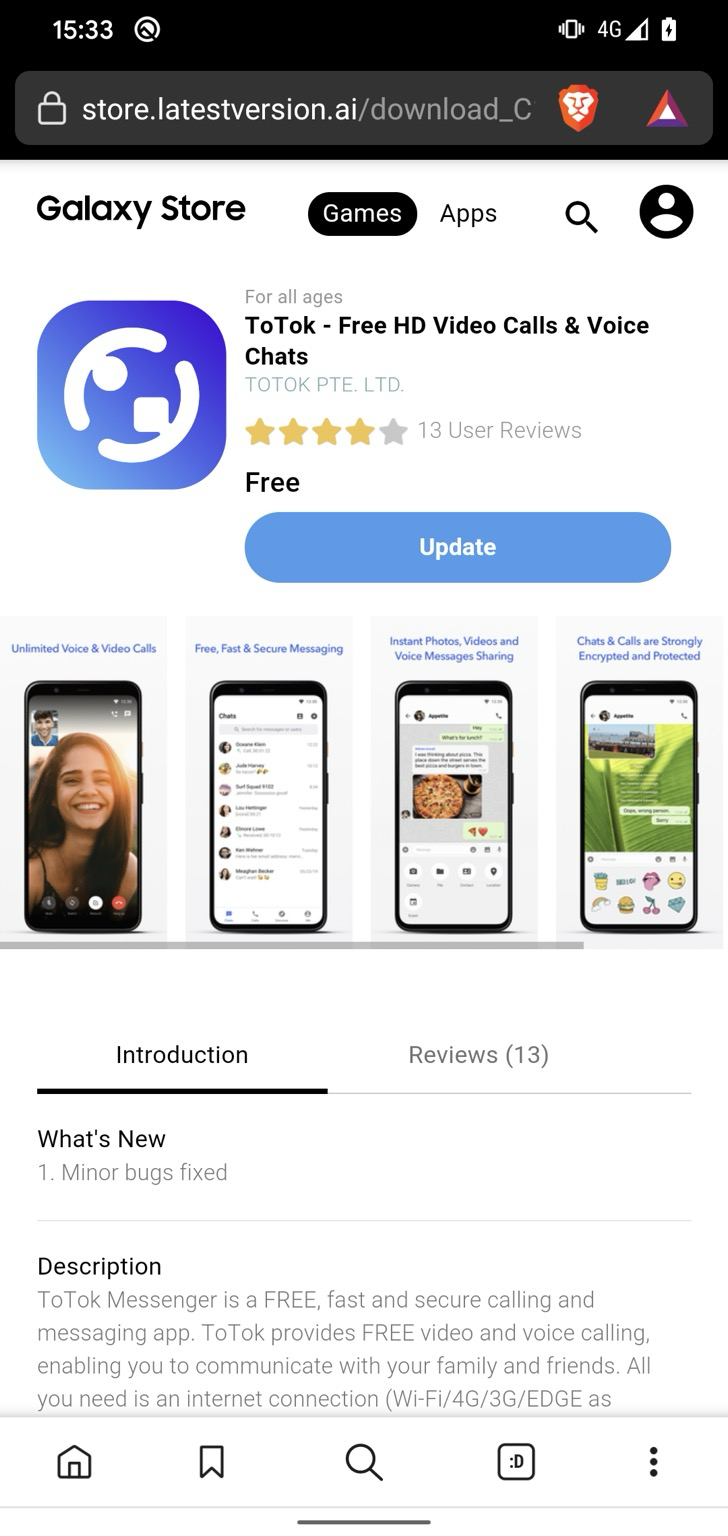
Android #ToSpy, the spyware used in the other campaign, masquerades solely as the ToTok app. It is distributed through phishing websites impersonating app distribution platforms, such as the Samsung Galaxy Store.
After compromising their targets, both ProSpy and ToSpy exfiltrate data in the background, including documents, media, files, and contacts. ToSpy in particular also targets .ttkmbackup files, suggesting a focus on chat history and app data.
Despite similar objectives and techniques, ESET tracks the two campaigns separately due to differences in infrastructure and delivery. Users should avoid downloading apps or plugins from unofficial sources, especially those claiming to enhance trusted services.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/prospytospy