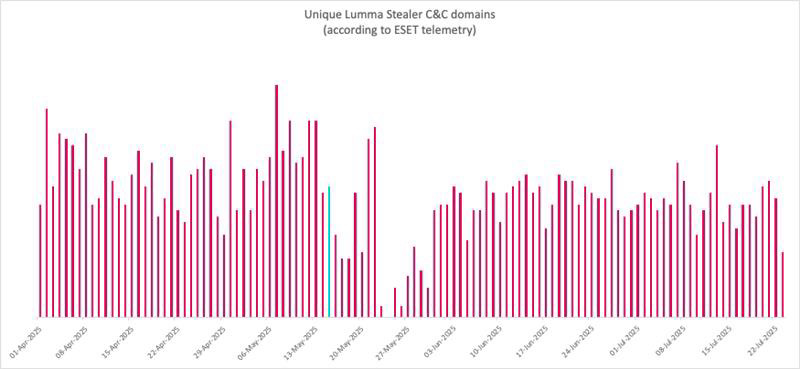
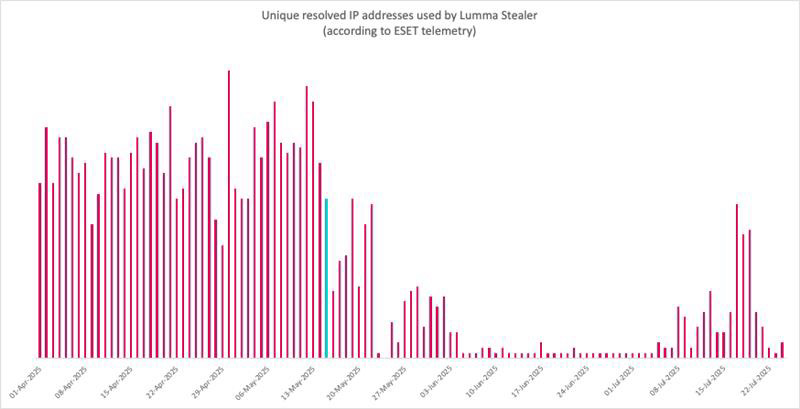
#BREAKING #ESETresearch can confirm the news of #Lumma Stealer's revival. ESET telemetry and botnet tracking show that operators are rebuilding their infrastructure, with their renewed activity reaching similar levels to those before the #disruption in May 2025.
Lumma Stealer operators are registering dozens of new domains weekly, resolving them primarily at nameservers located in RU. As seen with other threats in the past, this can complicate future attempts to disrupt its malicious operations.
In partnership with #Microsoft and other allies, ESET is tracking Lumma Stealer activity and continues to partially disrupt its operations, specifically by targeting its #Steam dead drop resolvers.
While ESET telemetry shows new Lumma Stealer builds weekly, their codebase hasn’t changed much since the takedown attempt. This suggests that the attackers had to focus on operational recovery instead of innovation.
C&C data show reduced activity around the disruption (marked in turquoise) but the number of new samples detected per day has seen only minimal changes, highlighting the continual risk.
For more info on Lumma Stealer and the disruption, read our blogpost from a few weeks back https://www.welivesecurity.com/en/eset-research/eset-takes-part-global-operation-disrupt-lumma-stealer/
Lumma Stealer operators are registering dozens of new domains weekly, resolving them primarily at nameservers located in RU. As seen with other threats in the past, this can complicate future attempts to disrupt its malicious operations.
In partnership with #Microsoft and other allies, ESET is tracking Lumma Stealer activity and continues to partially disrupt its operations, specifically by targeting its #Steam dead drop resolvers.
While ESET telemetry shows new Lumma Stealer builds weekly, their codebase hasn’t changed much since the takedown attempt. This suggests that the attackers had to focus on operational recovery instead of innovation.
C&C data show reduced activity around the disruption (marked in turquoise) but the number of new samples detected per day has seen only minimal changes, highlighting the continual risk.
For more info on Lumma Stealer and the disruption, read our blogpost from a few weeks back https://www.welivesecurity.com/en/eset-research/eset-takes-part-global-operation-disrupt-lumma-stealer/
2 media