#ESETresearch has uncovered a new #Android spyware campaign using novel romance scam tactics to target individuals in 🇵🇰 Pakistan, with an added social engineering element previously unseen in similar schemes. https://www.welivesecurity.com/en/eset-research/love-actually-fake-dating-app-used-lure-targeted-spyware-campaign-pakistan/
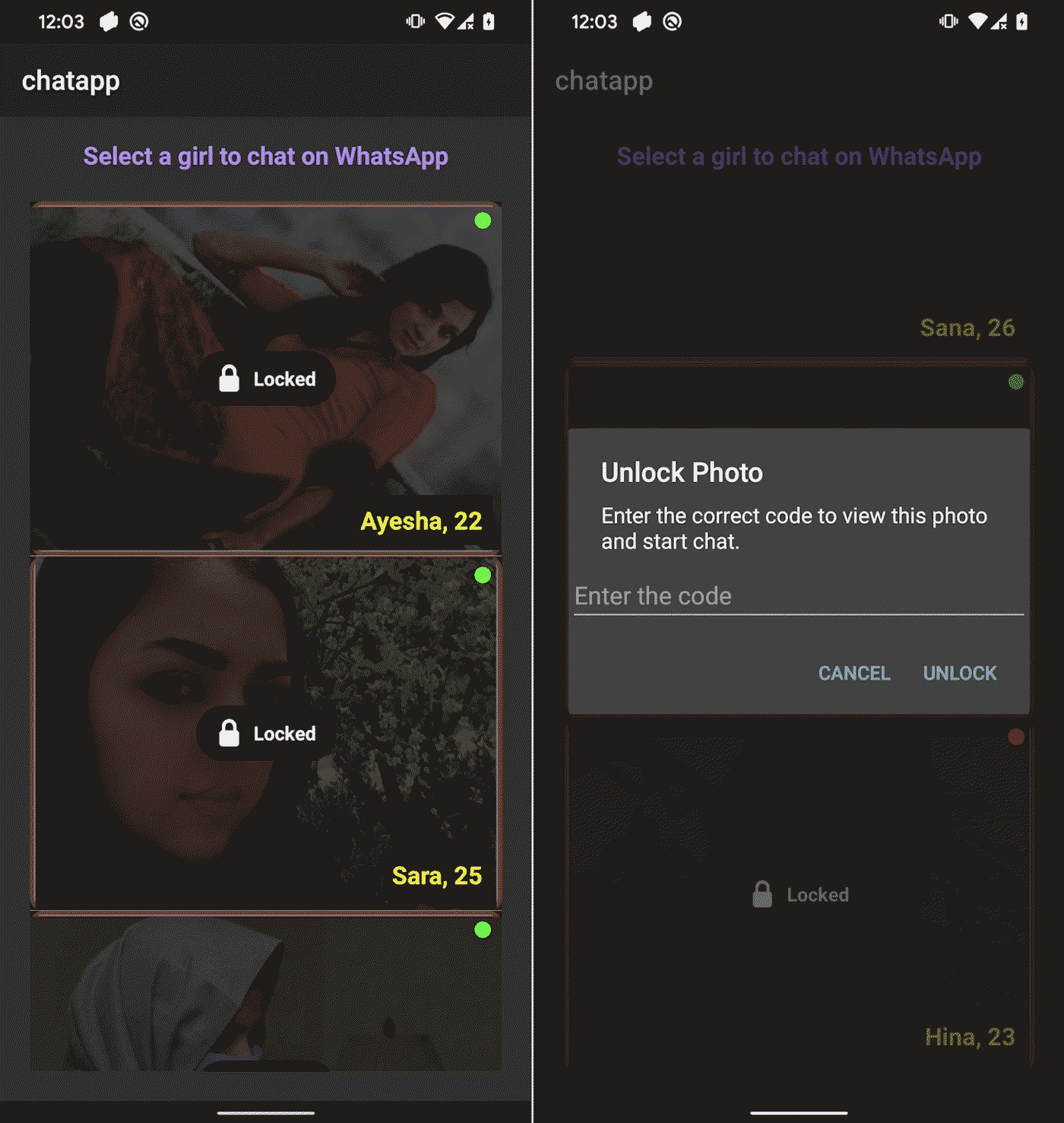
The spyware used in the campaign, which we named #GhostChat, uses the icon of a legitimate chat app. After installation from unknown sources, login credentials and unlock codes are required to access the app and individual chat profiles, respectively.
The credentials and codes are not processed by any server and are hardcoded in the app, implying that they are probably distributed along with the app by the threat actor.
This impression of personalization and exclusive access is rarely seen in mobile threat campaigns and suggests a highly targeted social engineering effort. Under its façade lies the true purpose of the app: data exfiltration.
Upon installation, GhostChat immediately requests permissions and begins exfiltrating data – even before login. It continuously monitors new images, scans for documents every five minutes, and exfiltrates sensitive information from the device.
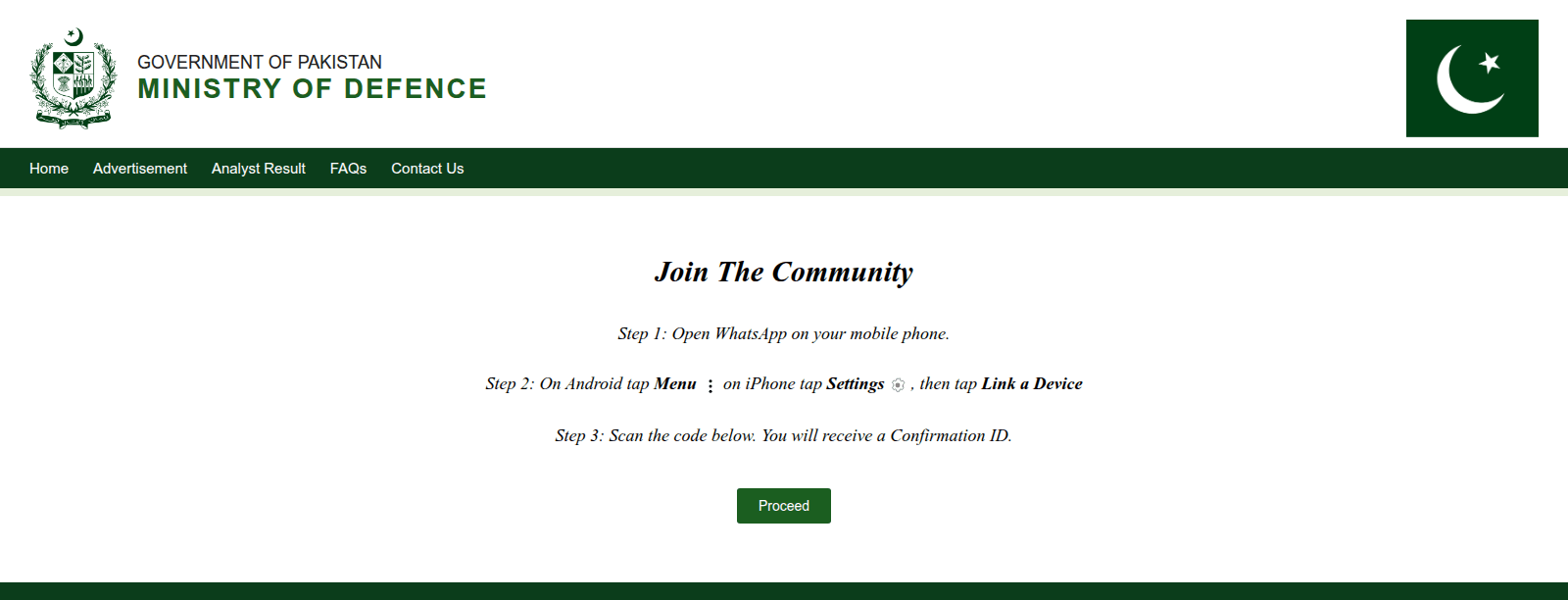
The GhostChat campaign is part of a broader, multiplatform, spy operation. In related activity, victims are lured into scanning QR codes on websites impersonating Pakistan’s Ministry of Defence, thereby giving the threat actors access to private #WhatsApp communications.
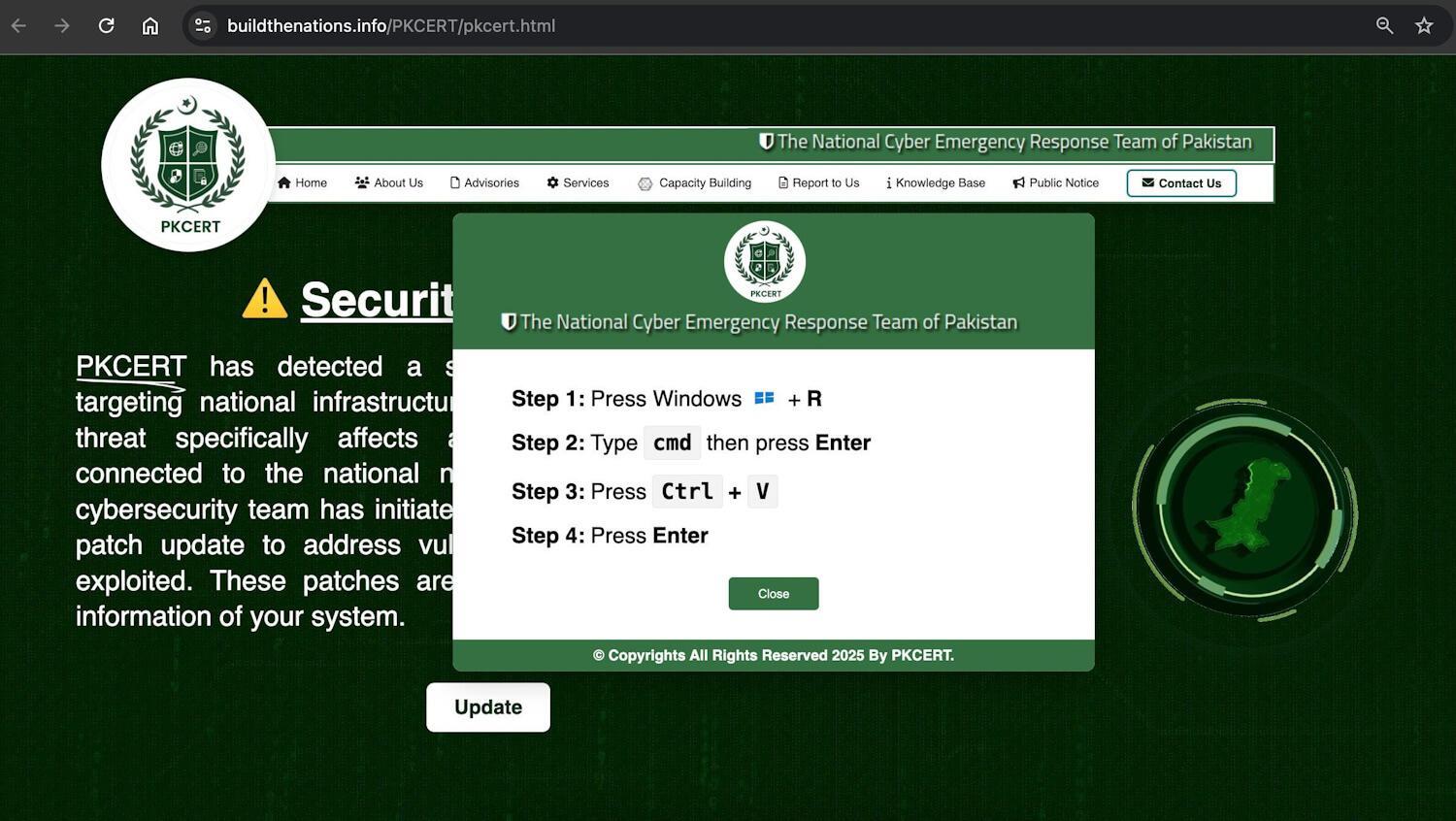
The same domain (buildthenations[.]info), also used to impersonate the Ministry of Defence website, mimics Pakistan’s Emergency Response Team and delivers a payload via #ClickFix, targeting desktop devices.
The operation blends mobile spyware, social engineering, and desktop exploitation, targeting users in 🇵🇰 Pakistan. Despite its specific targeting, there are insufficient similarities in TTPs to attribute this campaign to any known threat actor at this point.
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/ghostchat
Read the full analysis on WeLiveSecurity: https://www.welivesecurity.com/en/eset-research/love-actually-fake-dating-app-used-lure-targeted-spyware-campaign-pakistan/
3 media