As I wrote before (https://mastodon.bsd.cafe/@evgandr/115912395421390028) I tried to use TURN server for communication with my relatives, but failed to setup secure enough solution. So, I decided to try an old and reliable solution — Asterisk. With the help of a book "Asterisk: The Definitive Guide" from J.V. Meggelen & R. Bryant & L. Madsen, of course.
First, I was forced to build the asterisk package by myself (from ports, ofc), since the binary version from NetBSD repository compiled with the all DB support, except my favourite PostgreSQL database.
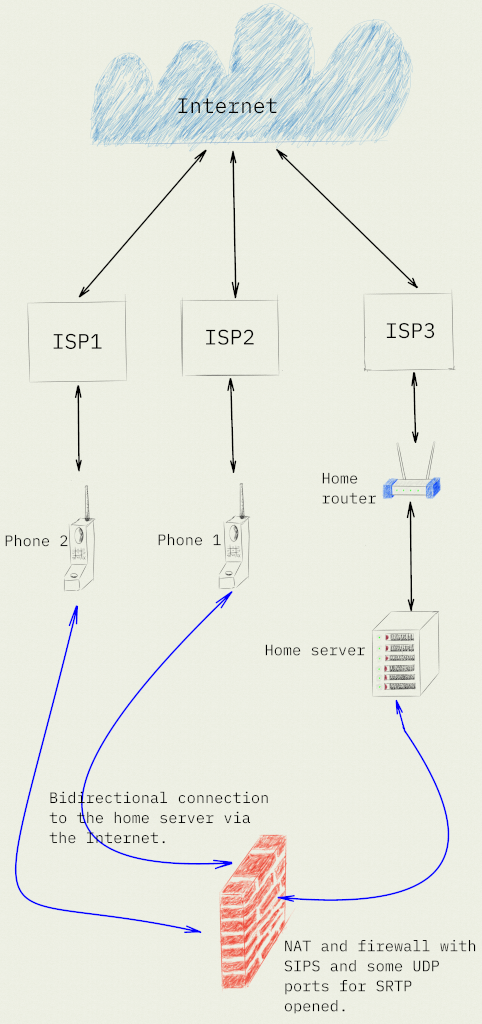
By the way, adding users and writing dialplan with the help of aforementioned book was not so hard as I expected  . Same for network setup. Since, I'm using PJSIP I just opened SIPS port and a range of UDP ports for RTP protocol on the my firewall. Despite, my home network hidden behind NAT on the router, there are no big problems with networking — end-user devices and an Asterisk server connected with use of simple star topology.
. Same for network setup. Since, I'm using PJSIP I just opened SIPS port and a range of UDP ports for RTP protocol on the my firewall. Despite, my home network hidden behind NAT on the router, there are no big problems with networking — end-user devices and an Asterisk server connected with use of simple star topology.
Surpisingly, the quality of the voice call is excellent comparing with service, provided by local cellular network operators. I suppose, that the secret in used codecs, or it is because there are not so much users (only 2) of my service.
Few days ago I successfully configured #coturn to have a TURN/STUN server for in-family calls. But … looks like bots or some bad guys constantly trying to connect to my TURN server to use it for something 😒
Of course, it is impossible, since anonymous access or any other access without right key is impossible. But, there are no IPs of attackers in the log file, even wth "Verbose" directive — only my local and public IPs and my server's hostname 
Maybe, there is some way to force coturn to display IP addresses of connected clients, so I could ban them all with fail2ban?