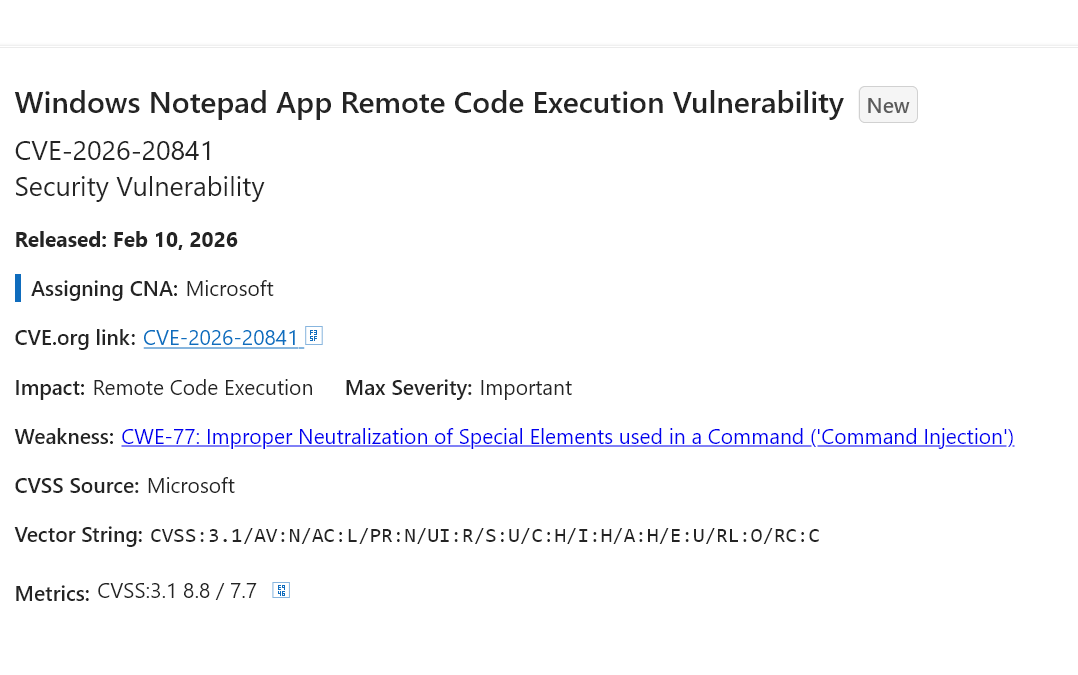
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore? 😭
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2026-20841
#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology