#ESETresearch has discovered a new 🇨🇳-aligned APT group, #LongNosedGoblin. This group focuses on cyberespionage and targets mainly governmental entities in Southeast Asia and Japan. https://www.welivesecurity.com/en/eset-research/longnosedgoblin-tries-sniff-out-governmental-affairs-southeast-asia-japan/
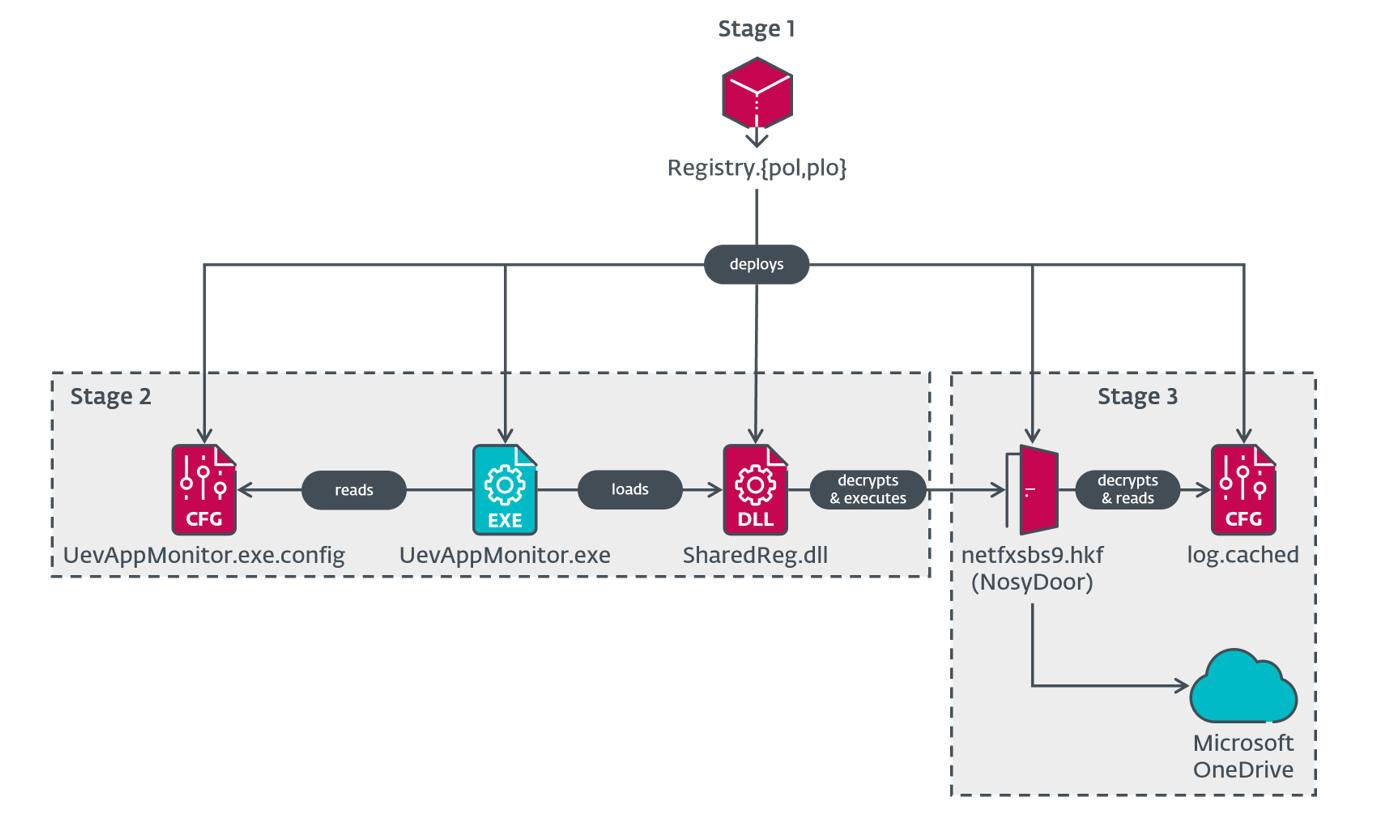
LongNosedGoblin uses Group Policy to deploy malware and move laterally across the compromised network. Its toolset consists mainly of malicious C#/.NET applications.
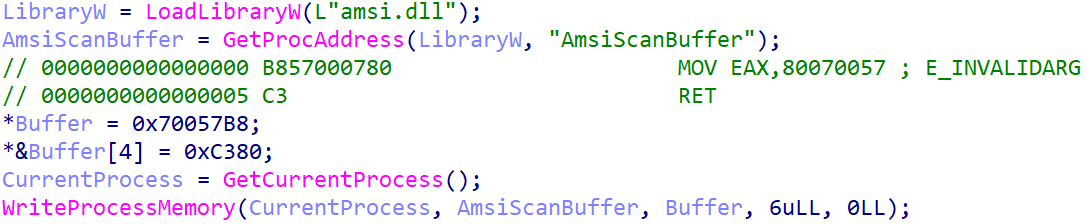
One of them is NosyHistorian, used to gather the victim’s browser history and decide where to deploy further malware. This includes NosyDoor, a backdoor that uses cloud services for C&C. NosyDoor also employs living-off-the-land techniques in its execution chain.
Our blogpost describes the discovery of LongNosedGoblin, goes over its known campaigns, and provides a detailed analysis of the group’s toolset.
We also recently presented these findings at #AVAR2025 in a talk titled Sniffing Around: Unmasking the LongNosedGoblin operation in Southeast Asia and Japan.
https://events.aavar.org/cybersecurity-conference/index.php/sniffing-around-unmasking-the-longnosedgoblin-operation-in-southeast-asia-and-japan/
IoCs available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/longnosedgoblin
2 media