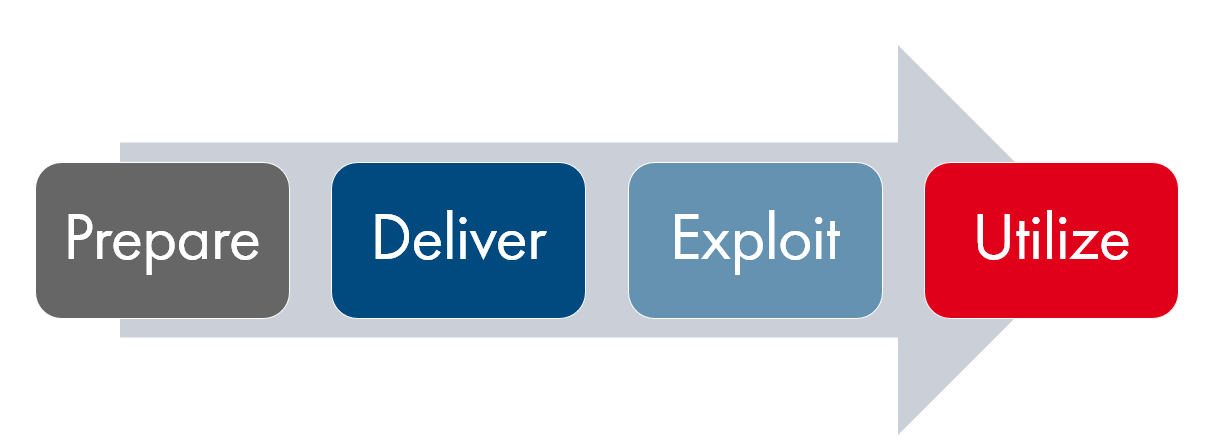
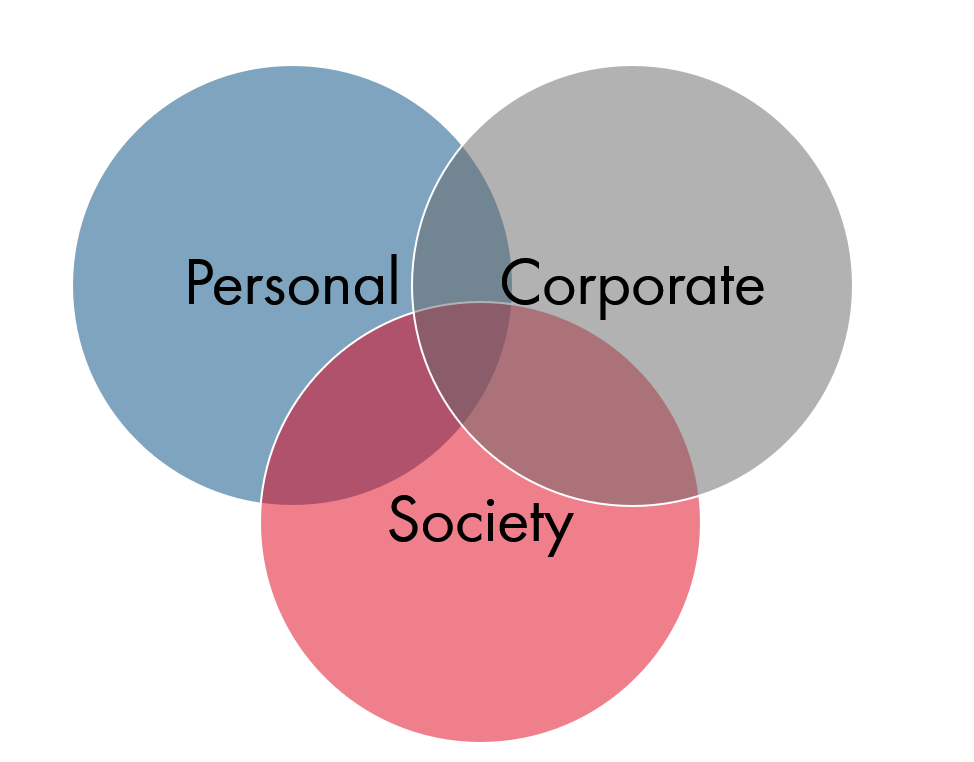
I have the challenge to give an overview about #cybersecurity in 5 minutes 😮
My idea is to combine personal as well as cooperate security. To give everyone something that makes them more secure individually and improve the corporate security posture. And i would also talk about current attacks
The problem is, it's just so much for 5 minutes.
To my question to you #cybersecurity experts and non-experts alike.
What would do you think needs to be in a 5 minutes overview? What would you like to hear about?