RE: https://infosec.exchange/@greynoise/116047942661766828
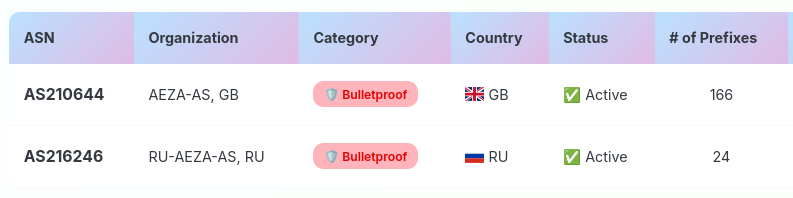
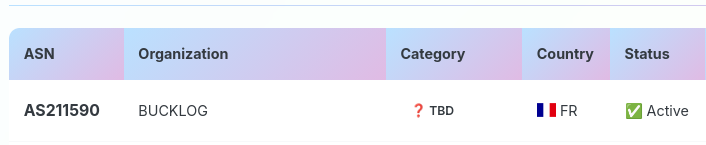
FWIW, if you were using the #GAYINT block list for your Ivanti RMM system, that IP on the bulletproof AS200593 would have been blocked. 
83% of observed Ivanti EPMM exploitation (CVE-2026-1281) traces to one bulletproof IP that isn't on any published IOC list. The IPs that are? VPN exits with zero Ivanti activity. We broke down who's actually doing this ⬇️ https://www.greynoise.io/blog/active-ivanti-exploitation