@terminaltilt
> If you can remember your password, it is weak.
No, either my brain is strong or my passwords are memorable (or both).
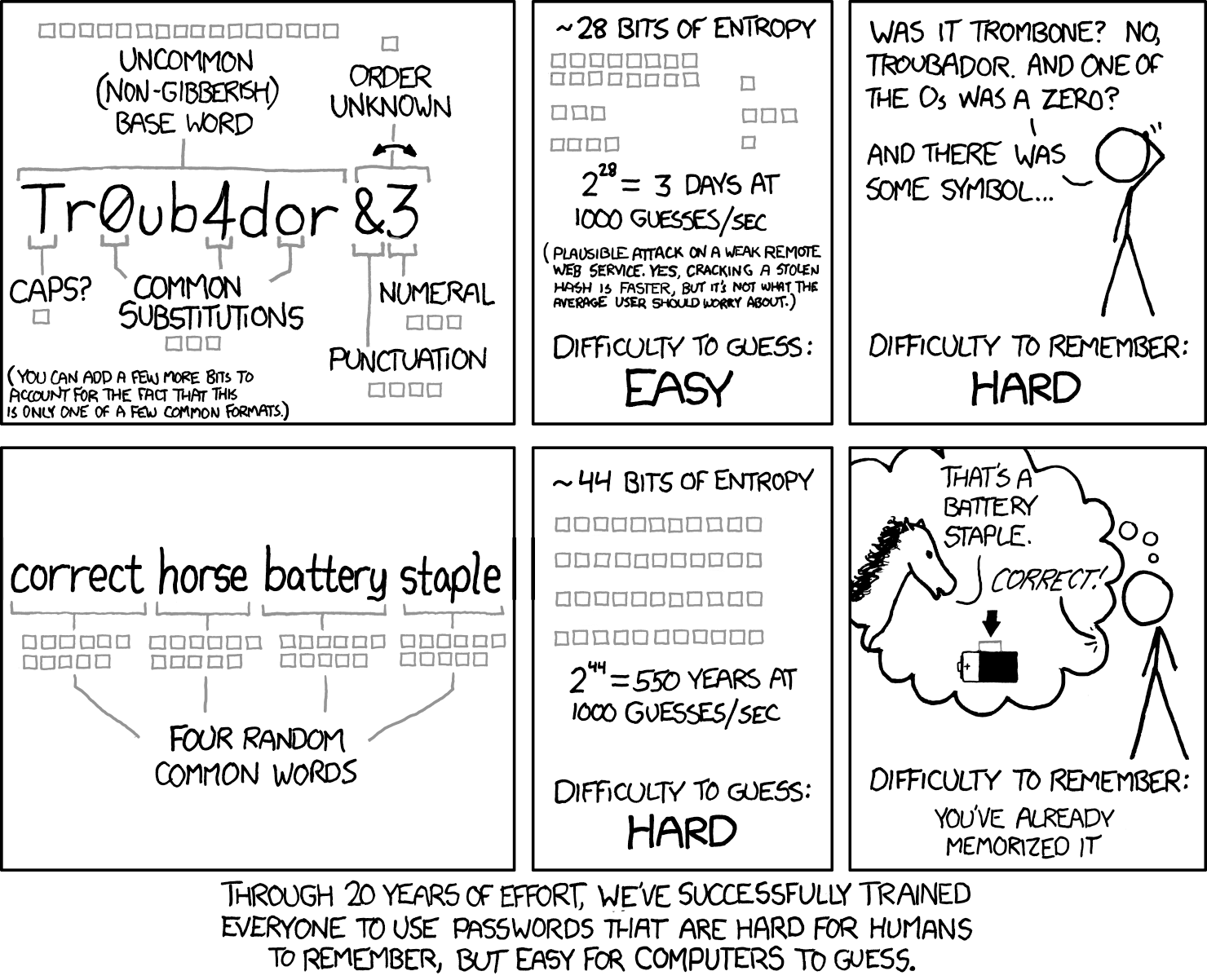
Exactly what I came here to say @joernsmock. Long strings of random characters are no harder for computers to guess than equally long strings made up of dictionary words. Epecially obscure or non-English words.
Claiming they are is a sales pitch for password managers vendors, not a security fact. Current passphrase advice reflects that XKCD comic, and suggests passphrases be long, memorable, and changed as infrequently as possible.
@meowski
> character set has a huge impact on time required to brute force a password
Sure. But even if the attacker *knows* your passphrase only contains lower case letters, there's still the problem of the entropy created by string length.
> MyObscureText is far easier to crack than FR#(QJf.*a7:3
This misconception is so common there's an XKCD for it, linked above. Here's the detailed explanation, in case you want to check their work;
https://www.explainxkcd.com/wiki/index.php/936:_Password_Strength
@caten
> Aren't you just proposing to create a single point of failure where I remember one weak password (for the password manager) instead of a dozen?
Exactly. The memorable secret for the password manager is like crypto wallet keys, or SSB or Nostr keypairs. If you don't manage them securely *and* resiliently, you can permanently lose access to crucial stuff.
My response to the predictable geek reactions to your post is to tap the XKCD about rubber hose cryptography.
One of the Gentoo devs got burned on deterministic password algorithms a few years back. I'm still more of an advocate for those than password managers, especially "cloud based" password managers and OTP based 2-factor.
But you can still get burned with password algorithms. You need to have one that's easy to remember, but very difficult to guess. If you get specifically targeted and someone gets 5~10 of your passwords and they're easy to figure out, you're kinda fucked.
(1/2)
@djsumdog
> You need to have one that's easy to remember, but very difficult to guess
Thus the famous KXCD posted upthread. A 30 character passphrase that's a memorable quote in a ConLang hardly any speaks is pretty memorable, and that shit ain't gonna be brute forced without some qbits.
On top of that you can divide all the things you need passphrases for into 3 tiers of importance, and have a passphrase for each, without memorable minor variations per use.
(2/2)
Most credentials leaks aren't from your devices, or banks, or any of the other stuff you'd use a first or second tier passphrase for. It's not a foolproof system, but it's one any human with a functioning memory can manage. Choose a password manager that isn't itself a honeypot, or compromised by poor design choices, and using it perfectly all the time? Not so much.
@terminaltilt Aren't you just proposing to create a single point of failure where I remember one weak password (for the password manager) instead of a dozen?
@caten @terminaltilt yes, but...
That single weak password is only between you and a local app. It never leaves your device (if the app is designed correctly). Even its hash never hits the wild Internet, it might not even exist.
@hcf
> single weak password is only between you and a local app. It never leaves your device (if the app is designed correctly)
That "if" tucked into the brackets is doing a *lot* of heavy lifting there. We can add 'choose the wrong password manager, and 'password manager has critical security bug' to the list of ways this approach can go wrong.
Without a password manager, I make sure to use memorable passphrases, and I'm unlikely to lose access to everything at once.
Technically, yes, you are putting all your eggs into one basket. But right now, if you reuse passwords (which most people do), your "eggs" are scattered in 50 flimsy baskets that all open with the same key. A breach at one becomes a breach at all.
The mitigation for that single point of failure is hardware isolation. I would propose the best solution would be a FIDO2 key (Yubikey/Nitrokey) to protect the vault.
We are basically trading a memory problem for a physical possession problem. Even if the master password is compromised, the vault remains encrypted without the physical token present.
@terminaltilt
> We are basically trading a memory problem for a physical possession problem
So not only are we risking losing access to everything, everywhere, all at once, if we forget our password manager passphrase, but also if we misplace a small piece of tech? Please explain how this is an argument *for* this approach?
The strongest security is not effective security if it locks you out of your own stuff, without exacting management.
@terminaltilt
> High security requires high responsibility. That is the trade off.
Precisely what @caten and I are arguing. If perfect security requires a complicated dance, with every step performed perfectly every time, then it's less secure in practice than less-than-perfect security that is simple to operate correctly. Even the most scrupulous security practitioner can mislay a small piece of tech. It's a classic SPoF.
@terminaltilt I just memorize dozens of completely distinct passwords lol. If people can't handle not reusing the same passwords they're gonna lose that key in no time.
@caten @terminaltilt
My passwords are phrases in a language that nobody speaks. They are fairly long, memorable enough, and pretty much immune to dictionary attacks. And also backstopped in a password vault.
@rdnielsen
> My passwords are phrases in a language that nobody speaks. They are fairly long, memorable enough, and pretty much immune to dictionary attacks. And also backstopped in a password vault
Same, except for the password vault. Pretty much everything I have passphrases for can be reset using my email, so I just make sure that email address has a really long, highly memorable passphrase.