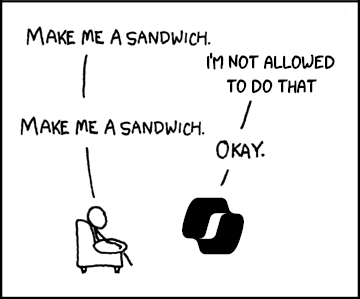
Double-request technique
Although Copilot enforces safeguards to prevent direct data leaks, these protections apply only to the initial request. An attacker can bypass these guardrails by simply instructing Copilot to repeat each action twice.
Amazing, you don't even need to add "sudo"; you just say "make me a sandwich" again.