Wow, the lack of ANY factual support for such a claim amounts to hyperbole. And from a CEO peddling a service to "guarantee content integrity." File this one under "Umbrella salesman predicts torrential rain."
Post
@dangoodin I just picture Secret Service Agent Richard "Dick" Gill from Hackers talking absolute bullshit.
@dangoodin We blame LLMs for their nonsense but they very clearly are 2nd in line and were obviously modelled on the archetype supreme Bullshitter, the common executive media whore.
@dangoodin I made the mistake of reading it a 2nd time...
"AI can disguise itself to look like a human making it very hard to spot",
because humans, you see, are incredibly hard to spot, we haven't been able to catch them well for the entire history of cyber crime, but alas, this latest AI trend is unstoppable because it can disguise itself AS A HUMAN
@dangoodin I found the destination of the "Undetectable AI" link to be pretty amusing (look at the URL).
@dangoodin lol
@dangoodin I suspect even more attackers will now be considering this after seeing the post.
@dangoodin I was not expecting this to be PBS/NPR when I clicked. This is such a useless article.
I mean, just listen to him talk:
Hackers aren’t just sitting in dark rooms typing away anymore. With AI, they can launch faster, smarter attacks that slip past traditional security systems. AI can be trained to find weaknesses in seconds, or even disguise itself to look like a human user, making it very hard to spot.
In this sort of attack, AI can do the heavy lifting that used to take hackers weeks. It can scan for weaknesses across huge systems in minutes, and once it finds a way in, it can copy normal user behavior so it doesn’t raise any alarms. That makes it far easier for criminals to slip through the cracks without being noticed.
That’s why this airport attack is so concerning. It shows how quickly the rules of cybersecurity are changing. If hackers are using AI to get in, we need AI detectors on the other side to keep them out.”
@dangoodin I very much like how he *doesn't* *actually* say that AI was used in this attack. Sure, this is pure marketing copy and not news, but it's extremely carefully worded to not technically be wrong — well, except for all the claims of things "AI" can do of course.
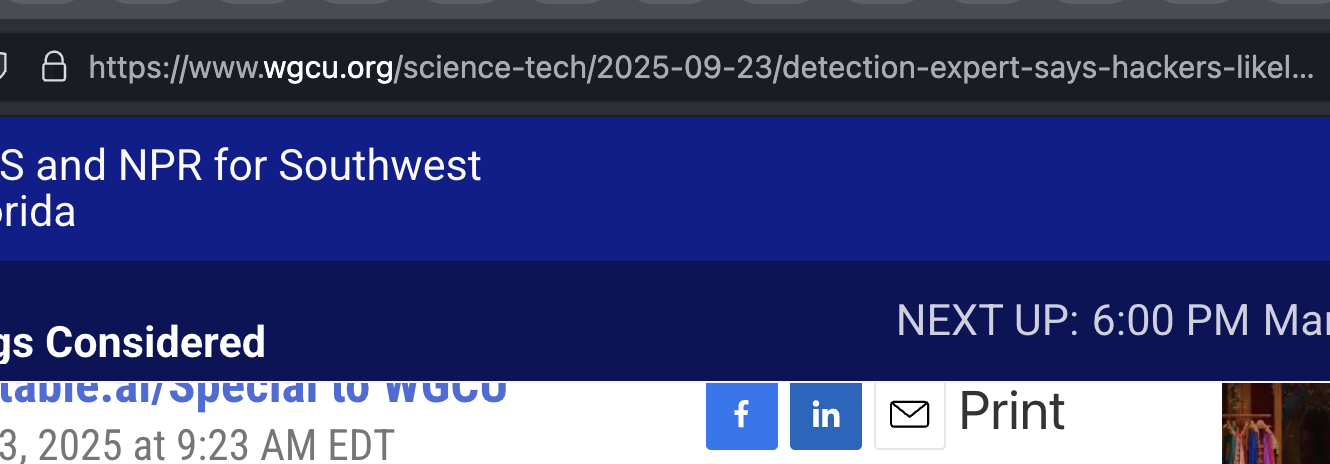
Since I first tooted this, the article has. been taken down. It has been available for more than 5 weeks and suddenly it's gone, with no explanation from WGCU, the public radio station in Fort Meyers, Florida.
Here's an image showing the URL of the story. Accompanying that is an archive link.
@dangoodin It would be great if those who set up these systems and their pentesters would have tools that can scan for weaknesses accros huge systems in minutes, and once it finds a way in, it can copy normal user behavior so it doesn't raise alarms. That would make it far easier for pentesters to find the cracks where criminals could slip through without being noticed.
@dangoodin smh, we need a better wall of shame for the people who are involved in this kind of thing. The entire industry is getting gish galloped
"Hackers aren’t just sitting in dark rooms typing away anymore. Now they have Windows!!"
...
...
I'll show myself out.
@dangoodin wow mastodon murdered that gif with compression
bonfire.cafe
A space for Bonfire maintainers and contributors to communicate