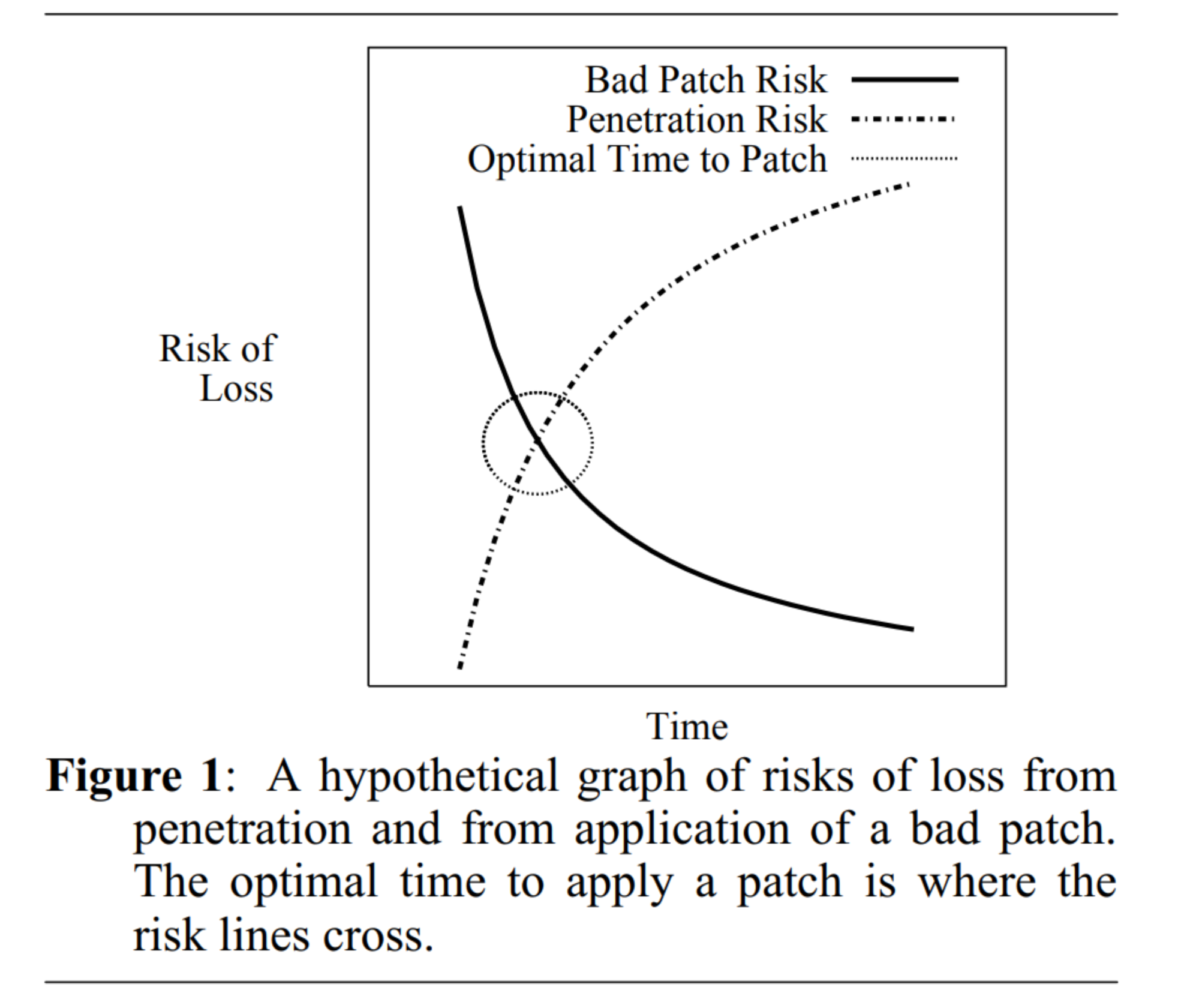
⚠️ Patch Tuesday update makes Windows PCs refuse to shut down
「 Microsoft says that entering the command "shutdown /s /t 0" at the command prompt will, in fact, force your PC to turn off, whether it wants to or not 」
https://www.theregister.com/2026/01/16/patch_tuesday_secure_launch_bug_no_shutdown/