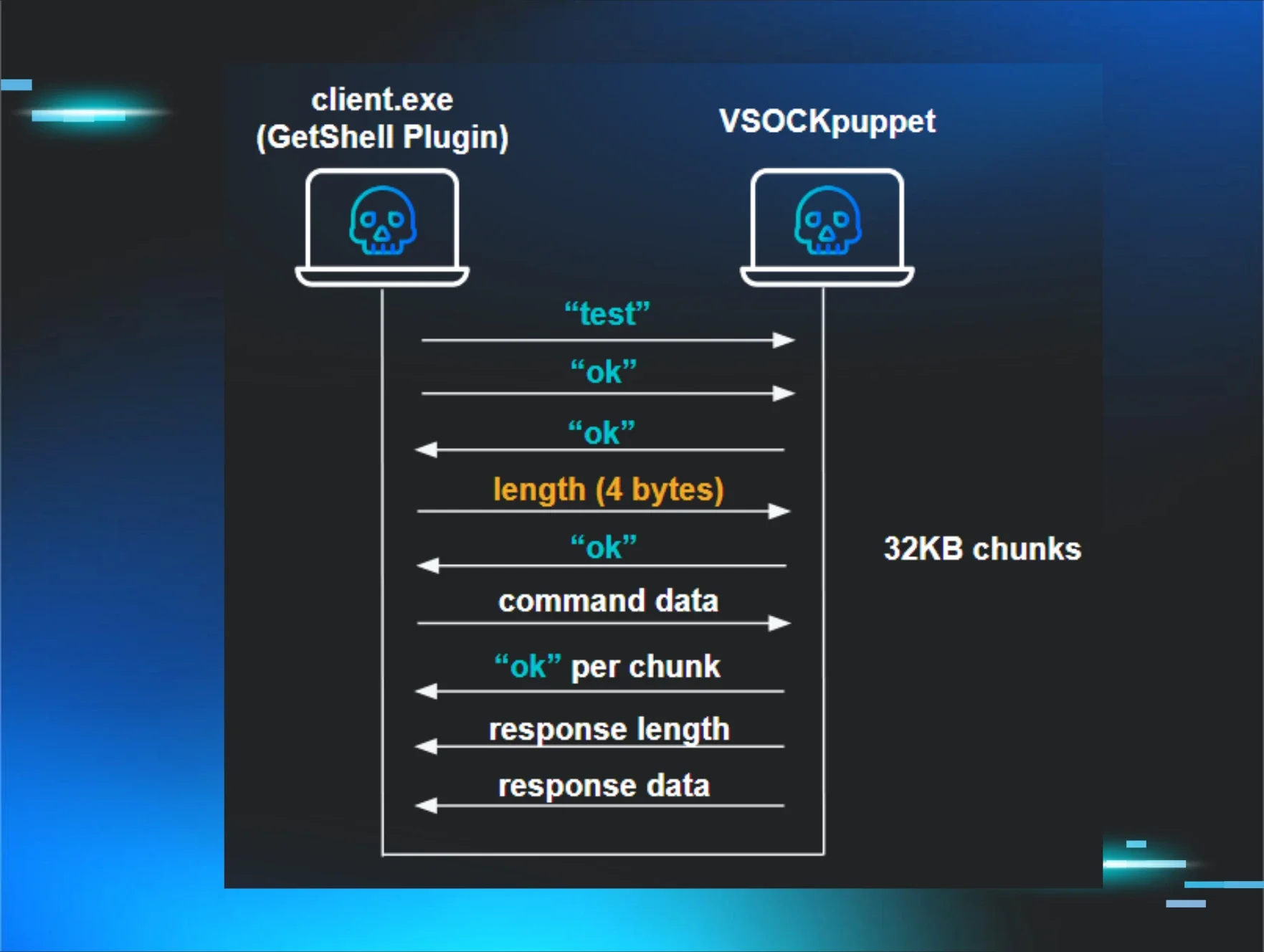
Huntress writes about VMware exploitation and boy, they have gone all in on the details.
https://www.huntress.com/blog/esxi-vm-escape-exploit
This is well worth reading. Exploit was likely developed almost a year before use. (Or something like that...)