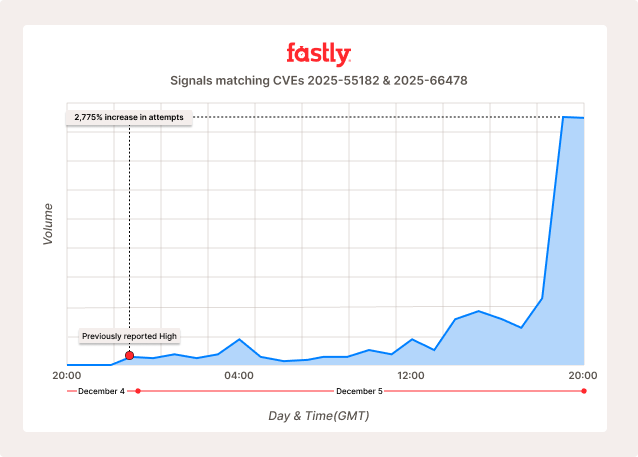
Another #React2Shell Update: Fastly saw a 2,775% increase in attack activity across our global network between the peak we reported yesterday (Dec. 4th) and 20:00 UTC today (Dec. 5th).
⚠️ This in-the-wild evidence suggests attackers are relentlessly probing for vulnerable applications at scale. ⚠️
It is worth your time to verify, not just trust, that you have zero exposure, and then drop everything to patch.
After the POC publicly dropped around 21:04 UTC yesterday (Dec. 4th), @fastlydevs detected what appeared, at the time, like a sharp escalation in attack activity.
In the 24 hours since then, the number of requests triggering our NGWAF signals for React2Shell exploded by 2,775% (as shown in the graph).
🌎 Fastly's Security Research team verified that select public PoCs grant attackers the single-step ability to execute commands, exfiltrate data, and gain write access on vulnerable servers.
This means cybercriminals and nation state actors alike face an alluring ROI, which is likely to motivate them to invest in weaponizing and operationalizing this at scale.
We are sharing this intelligence not to sow fear, but to reinforce the undeniable, urgent necessity of patching at this point. We also have a few updates for our customers:
🛡️ Fastly's teams expanded our Virtual Patch for CVE-2025-55182 to detect scan/probe activity and attempts to circumvent our NGWAF protections.
🛠️ We discovered the built-in "Attack Tooling" signal in our NGWAF already detects scanners that emerged in the past 24h to probe for vulnerable apps; we suggest customers investigate any requests that triggered this signal, as it may indicate React2Shell activity.
🤖 Fortuitously, Fastly's Bot Management product flagged some react2shell attack tooling as a "Suspected Bad Bot," offering organizations another layer of defense here.
At this time, Fastly's goal is to provide our customers with breathing room to patch.
The best available fix at this time is to update your apps to the applicable patched versions. We are at the point where it is no longer "if," or possibly even "when," but "how often"?
We will continue monitoring global attack activity, investing in additional mitigations for our customers, and sharing intel with the public community.