Several months ago, I found a #vulnerability from #MantisBT - Authentication bypass for some passwords due to PHP type juggling (CVE-2025-47776).
Any account that has a password that results in a hash that matches ^0+[Ee][0-9]+$ can be logged in with a password that matches that regex as well. For example, password comito5 can be used to log in to the affected accounts and thus gain unauthorised access.
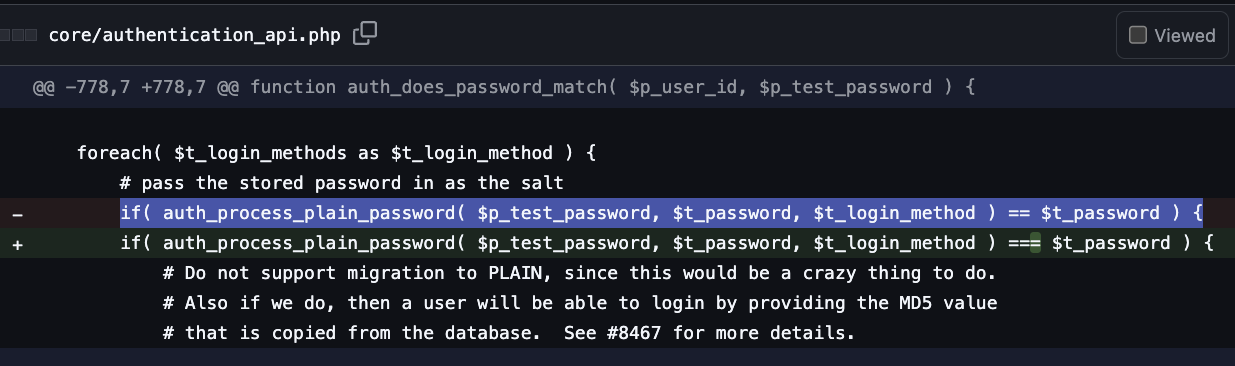
The root cause of this bug is the incorrect use of == to match the password hash:
if( auth_process_plain_password( $p_test_password, $t_password, $t_login_method ) == $t_password )
The fix is to use === for the comparison.
This vulnerability has existed in MantisBT ever since hashed password support was added (read: decades). MantisBT 2.27.2 and later include a fix to this vulnerability. https://mantisbt.org/download.php