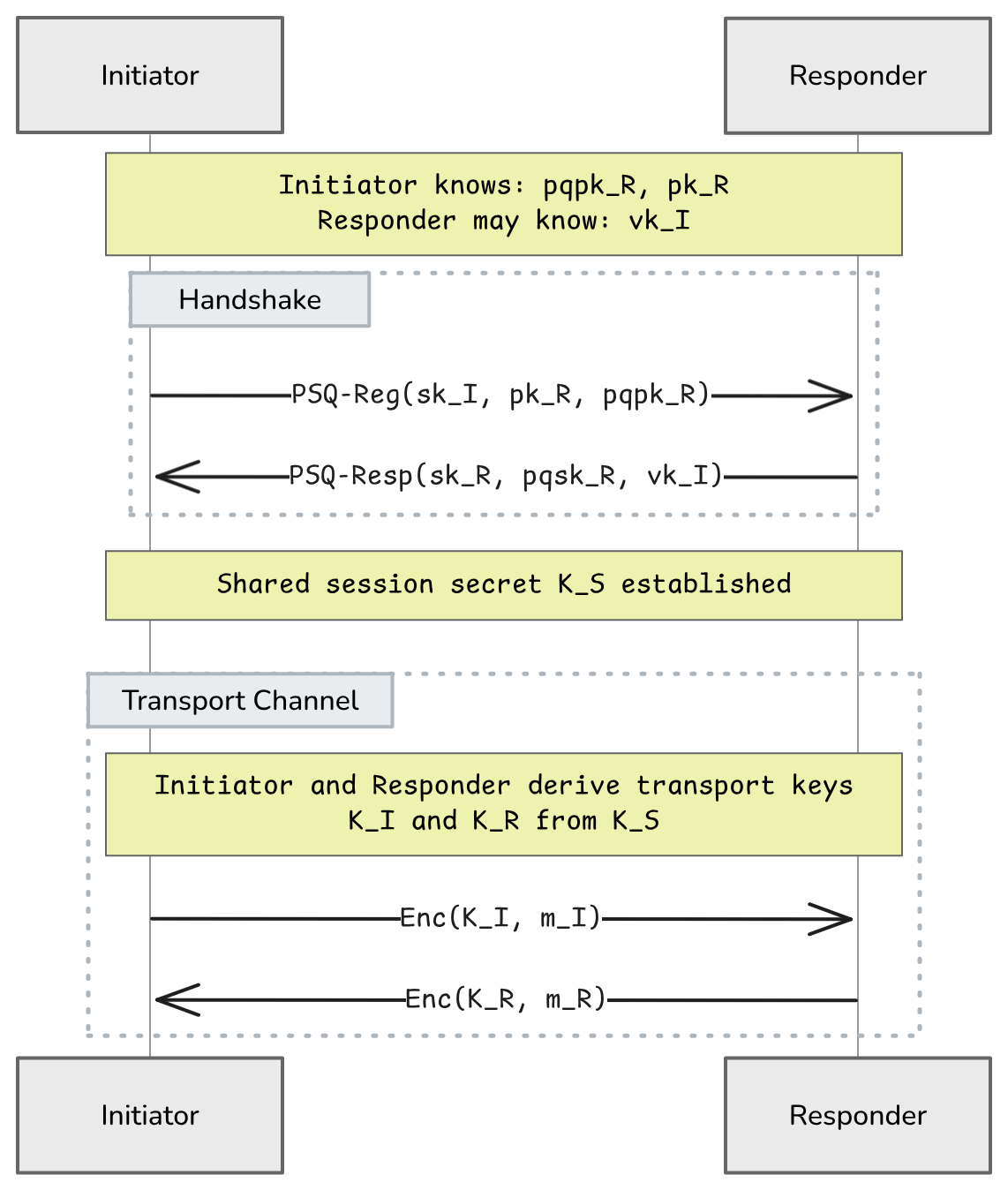
1/
RE: https://mastodon.social/@reiver/115945290105913697
Right now, Fediverse IDs resolve to HTTPS URLs.
For example, the Fediverse ID:
@reiver@mastodon.social
Resolves to HTTPS URL:
https;//mastodon·social/users/reiver
...
If we wanted cryptographic public-keys to serve as a basis of Identity on the Fediverse, then —
We would (similarly) also need a Fediverse ID to resolve to one or more cryptographic public-keys
...
#ActivityPub #Cryptography #FediDev #FediDevs #Fediverse #JSONLD
Cryptographic public-keys are one way that one can have an identity (on the Fediverse, and elsewhere) while also having privacy — through a pseudonymous identity.
Yes, we have Fediverse IDs such as:
@joeblow@example.com
But a (non-delegated) public-key can function as a PORTABLE form of identity on the Fediverse.
#ActivityPub #Cryptography #Fedidev #Fedidevs #Fediverse #JSONLD
2/
RE: https://mastodon.social/@reiver/115945290105913697
The resolving of a Fediverse ID to one or more cryptographic public-keys could happen via the activity-file for the user.
A JSON-LD namespace (separate from ActivityPub) could put the cryptographic public-keys into the activity-file.
But, I think we would need more information than what the 2 current methods for including cryptographic public-keys currently support.
#ActivityPub #Cryptography #FediDev #FediDevs #Fediverse #JSONLD